What software is sold on usage based theory – What software is sold on usage-based theory? This question unveils a fascinating facet of the software industry, moving beyond traditional licensing models. Instead of fixed prices, usage-based software pricing hinges on the actual consumption of the software’s resources or features. This approach offers both advantages and disadvantages for both vendors and customers, creating a dynamic market landscape shaped by factors like scalability, metering accuracy, and the complexities of contract law.
Understanding the nuances of usage-based pricing is crucial for anyone involved in the development, purchase, or management of software applications.
This exploration delves into the core principles of usage-based licensing, examining various pricing models and the technical infrastructure needed to effectively track and monitor software usage. We’ll also consider the legal implications of such agreements, addressing potential disputes and outlining best practices for contract drafting. Finally, we’ll look at the customer perspective, market trends, and the future of this evolving area of software development and distribution.
Defining Usage-Based Software Licensing
Usage-based software licensing represents a significant departure from traditional licensing models. Instead of a fixed price for perpetual access or a recurring subscription fee, the cost is directly tied to the actual utilization of the software. This approach offers flexibility and scalability, aligning software costs with business needs and potentially reducing overall expenditure. The core principle is a pay-as-you-go system, ensuring that customers only pay for the resources they consume.Usage-based licensing models operate on the premise of quantifiable metrics reflecting software usage.
This allows for a dynamic pricing structure where the cost fluctuates according to the level of software engagement. This contrasts sharply with traditional models that often involve a fixed upfront investment or a predictable recurring payment regardless of actual usage.
Metrics for Measuring Software Usage
Several key metrics are employed to quantify software usage and determine licensing fees. The selection of appropriate metrics is crucial and depends heavily on the specific software and its intended application. Incorrect metric selection can lead to inaccurate cost estimations and potential dissatisfaction for both the vendor and the customer.
- Number of Users: This metric is straightforward and commonly used, particularly for applications with a strong emphasis on individual user accounts. The cost is calculated based on the number of concurrent or total users accessing the software within a defined period.
- Number of Transactions: Transaction-based licensing is suitable for applications where the core functionality revolves around discrete actions or events. Examples include payment processing systems, e-commerce platforms, or order management software. The cost is directly proportional to the number of transactions processed.
- Data Volume: This metric is relevant for applications handling large datasets, such as data warehousing, analytics, or cloud storage solutions. The licensing cost scales with the amount of data processed, stored, or transferred.
- Processing Power: For computationally intensive applications, the amount of processing power consumed can serve as a usage metric. This could involve CPU cycles, memory usage, or GPU time. This metric is commonly used in high-performance computing environments.
- API Calls: In software-as-a-service (SaaS) models, the number of API calls made by integrated applications can serve as a usage metric. This reflects the extent of interaction with the core software and allows for granular cost control.
Comparison with Traditional Licensing Models
Understanding the differences between usage-based licensing and traditional models is essential for selecting the appropriate licensing strategy. Each model presents distinct advantages and disadvantages depending on the specific context.
| Feature | Usage-Based Licensing | Perpetual Licensing | Subscription Licensing |
|---|---|---|---|
| Cost Structure | Variable, based on usage | One-time upfront cost | Recurring fixed fee |
| Access | Dependent on usage | Unlimited, perpetual access | Access granted for duration of subscription |
| Flexibility | High; scales with needs | Low; fixed cost regardless of usage | Moderate; typically fixed term but can be adjusted |
| Predictability | Lower; cost varies with usage | High; cost is fixed | High; cost is fixed for subscription term |
| Risk | Potential for unpredictable costs | High initial investment risk | Lower risk; predictable recurring cost |
Types of Software Utilizing Usage-Based Pricing
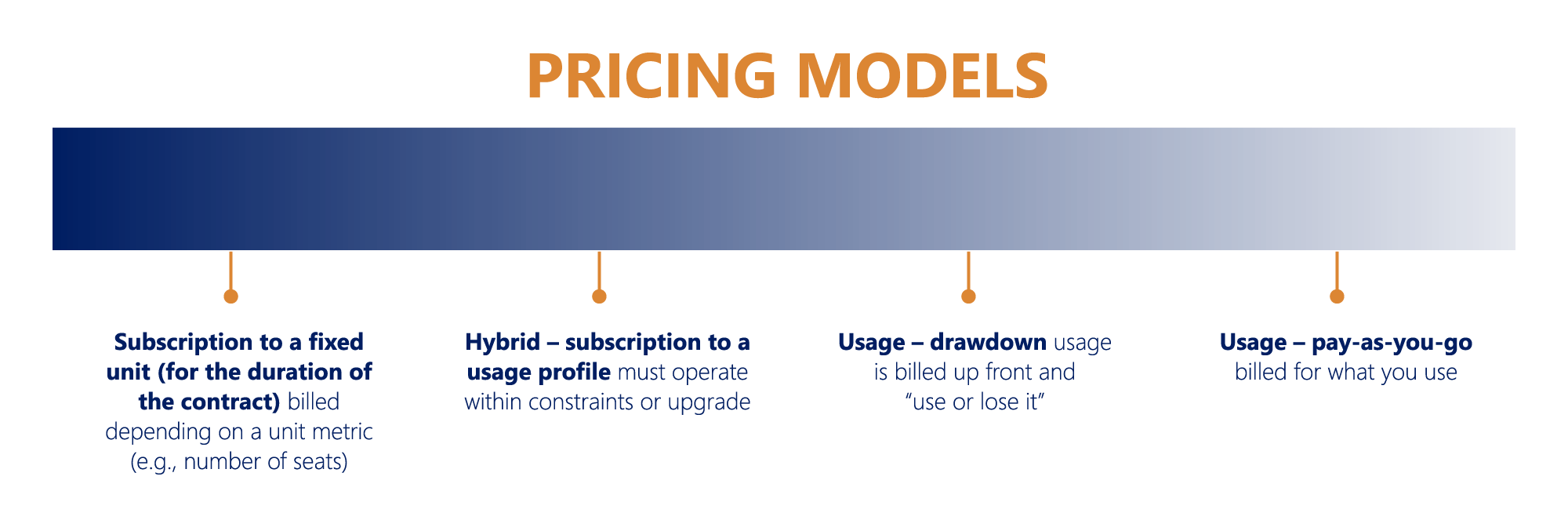
Usage-based pricing, also known as pay-as-you-go or consumption-based pricing, is a licensing model where customers pay only for the resources or features they actually use. This contrasts with traditional licensing models that charge a fixed fee regardless of usage. This model is increasingly prevalent across various software categories, driven by the need for flexible and scalable solutions. The following sections detail five distinct categories of software commonly employing this pricing structure.
Cloud Storage Services, What software is sold on usage based theory
Cloud storage services represent a prominent category utilizing usage-based pricing. Providers charge based on the amount of data stored, the bandwidth consumed for data transfer, and sometimes additional features like data replication or security enhancements. This model allows businesses and individuals to scale their storage needs up or down as required, paying only for what they use. Examples include Amazon S3, Google Cloud Storage, and Microsoft Azure Blob Storage.
The advantages include scalability and cost-effectiveness for fluctuating storage needs. Disadvantages may include unexpected cost increases if usage surpasses projections and potential complexities in managing and monitoring storage costs.
Software as a Service (SaaS) Applications
Many SaaS applications utilize usage-based pricing models, often tiered according to the number of users, features accessed, or the volume of data processed. Examples include CRM platforms like Salesforce, project management tools like Asana, and communication platforms like Slack. The advantages of usage-based pricing in SaaS are its flexibility, allowing businesses to scale their subscriptions based on growth and needs.
Disadvantages can include potential cost overruns if usage unexpectedly increases and the need for careful monitoring of usage to optimize costs.
Database Management Systems (DBMS)
Usage-based pricing is increasingly common for cloud-based DBMS. The cost is often determined by factors like the amount of data stored, the number of queries executed, the storage capacity used, and the computational resources consumed. Examples include Amazon RDS, Google Cloud SQL, and Microsoft Azure SQL Database. Advantages include scalability and cost optimization for databases with fluctuating demands.
Disadvantages include the complexity of accurately predicting costs and potential difficulties in optimizing queries to minimize expenses.
Application Programming Interfaces (APIs)
Many API providers employ usage-based pricing models, charging based on the number of API calls made, the volume of data transferred, or the processing power consumed. Examples include payment gateways like Stripe and mapping APIs like Google Maps Platform. Advantages include precise cost control, paying only for actual API usage. Disadvantages include potential cost volatility if usage patterns fluctuate significantly and the need for thorough API usage monitoring and optimization.
Many software companies are shifting to usage-based pricing models, billing customers based on actual consumption. This approach is particularly relevant for SaaS applications; a prime example of this is the functionality found in a saas knowledge base example , where features like search queries or support ticket submissions might be metered. Ultimately, the success of usage-based pricing hinges on the software’s ability to accurately track and bill for consumption, making it a complex but potentially lucrative strategy for software vendors.
Business Intelligence (BI) and Analytics Platforms
Usage-based pricing is applied to many BI and analytics platforms. Pricing may be based on the amount of data processed, the number of users, the features utilized, and the computational resources consumed during analysis. Examples include platforms like Tableau and Qlik Sense (although they also offer subscription models). The advantages include cost efficiency as users only pay for the resources they use for analysis.
Disadvantages include potential cost increases if data volumes or analysis complexity increase unexpectedly and the need for efficient data management to optimize costs.
Pricing Models in Usage-Based Software
Usage-based software licensing necessitates a pricing structure that accurately reflects the value derived by the customer based on their consumption. Several models exist, each with its advantages and disadvantages, impacting both customer acquisition and vendor profitability. The choice of model significantly influences the overall business strategy and market positioning.
Tiered Pricing
Tiered pricing structures offer varying levels of service or access based on usage volume. This approach allows businesses to cater to diverse customer needs and budgets. A typical tiered model might offer a basic plan with limited features and usage allowances, a standard plan with increased capabilities, and a premium plan with unlimited or significantly higher usage limits.
The pricing for each tier increases incrementally, reflecting the increased value provided. For example, a cloud storage service might offer a 10GB tier for $5/month, a 100GB tier for $20/month, and an unlimited tier for $50/month. This model balances accessibility with revenue generation, allowing for customer segmentation and growth potential.
Pay-As-You-Go
Pay-as-you-go (PAYG) pricing is characterized by billing customers solely for the resources consumed. This eliminates upfront costs and subscription fees, offering flexibility and scalability. Customers only pay for what they use, making it attractive for projects with unpredictable or fluctuating demands. However, PAYG models require robust metering and billing systems to track resource usage accurately. Examples include cloud computing services where compute time, storage, and bandwidth are billed hourly or daily, and mobile phone plans where usage is based on calls, texts, and data consumed.
The simplicity and transparency of PAYG appeal to many customers, while simultaneously requiring sophisticated backend systems to manage billing and resource allocation efficiently.
Volume Discounts
Volume discounts incentivize higher usage by offering reduced per-unit pricing for larger consumption volumes. This strategy encourages customer loyalty and potentially increases overall revenue, even with reduced per-unit prices. The discount structure can be linear or tiered, offering progressively larger discounts for increasing usage thresholds. For example, a software application might charge $1 per transaction for the first 1000 transactions, $0.90 per transaction for 1001-5000 transactions, and $0.80 per transaction for more than 5000 transactions.
The effectiveness of volume discounts hinges on accurately predicting the elasticity of demand and balancing revenue maximization with customer acquisition and retention.
Hypothetical Pricing Model: Project Management Software
Consider a new usage-based project management software application. The pricing model could be tiered, offering three plans:
| Plan | Users | Projects | Storage (GB) | Price/Month |
|---|---|---|---|---|
| Basic | 5 | 2 | 10 | $25 |
| Standard | 10 | 5 | 50 | $75 |
| Premium | Unlimited | Unlimited | Unlimited | $200 |
Cost Breakdown (per user): Development and maintenance costs are estimated at $100,000 annually. Customer support and infrastructure costs are estimated at $50,000 annually. Assuming 1000 users across all plans, the annual cost per user is approximately $150. This cost is spread across the pricing tiers, with the premium tier contributing the most to profitability.
Profitability Comparison: Example
Let’s compare the profitability of tiered pricing versus a pay-as-you-go model for a hypothetical document storage service. Assuming a fixed cost of $10,000 per month and a variable cost of $0.01 per GB stored:
Tiered Pricing: Three tiers (10GB/$5, 100GB/$20, Unlimited/$50). With 500 users at 10GB, 250 users at 100GB, and 250 users at unlimited (averaging 500GB), monthly revenue would be approximately $22,500, yielding a profit of $12,500.
Pay-As-You-Go: Charging $0.01 per GB. With the same usage pattern as above, monthly revenue would be approximately $17,500, yielding a profit of $7,500.
This example demonstrates that, in this specific scenario, the tiered pricing model is significantly more profitable. However, the optimal model depends heavily on factors such as customer demand elasticity, competitive landscape, and operational costs.
Legal and Contractual Aspects
Usage-based software licensing introduces unique legal complexities that require careful consideration during contract drafting and negotiation. A well-structured license agreement is crucial for mitigating potential disputes and ensuring a clear understanding of the rights and obligations of both the software provider and the licensee. This section details key legal considerations, best practices for defining usage metrics, and strategies for handling disputes related to usage calculations and billing.
Key Legal Considerations in Usage-Based Software License Agreements
The following five key legal considerations are paramount when drafting usage-based software license agreements. Ignoring these aspects can lead to significant legal ramifications for both parties involved.
| Legal Consideration | Potential Ramifications if Neglected |
|---|---|
| Definition of “User” and “Usage” | Disputes over the number of users or the definition of a single usage event, leading to inaccurate billing and potential legal action for breach of contract. This could involve significant financial losses for either party. |
| License Grant Limitations Tied to Usage | Failure to clearly define usage limits can result in disputes over exceeding the permitted usage, leading to potential termination of the license and legal action for breach of contract. The licensee might face penalties or be forced to renegotiate the agreement at unfavorable terms. |
| Data Privacy Implications of Usage Monitoring | Insufficient consideration of data privacy regulations (e.g., GDPR, CCPA) regarding the collection and processing of user data for usage monitoring purposes could lead to hefty fines and reputational damage. The software provider could face lawsuits from users or regulatory bodies. |
| Governing Law and Jurisdiction | Ambiguity regarding the governing law and jurisdiction for resolving disputes can create uncertainty and complicate the enforcement of the agreement. This can lead to protracted and costly litigation, with unfavorable outcomes depending on the chosen jurisdiction. |
| Dispute Resolution Mechanisms | Lack of clearly defined dispute resolution mechanisms (e.g., arbitration, mediation) can result in lengthy and expensive court proceedings. The lack of a predefined process can significantly increase costs and uncertainty for both parties. |
Importance of Clear and Unambiguous Usage Metric Definitions
Precisely defining usage metrics is fundamental to avoiding disputes. Ambiguous definitions can lead to conflicting interpretations and costly litigation.
Examples of ambiguous usage metrics and their potential for dispute:
- “Number of active users”: The definition of “active” might be unclear, leading to disputes about whether a user’s occasional login constitutes “active” usage.
- “Volume of data processed”: The units of measurement (bytes, kilobytes, etc.) and the methods for calculating data volume need to be clearly defined to avoid discrepancies.
- “Number of transactions”: The definition of a “transaction” might be open to interpretation, leading to disagreements about what constitutes a single transaction and how it should be counted.
Best practices for defining usage metrics include:
- Use specific, measurable, achievable, relevant, and time-bound (SMART) metrics. For example, instead of “high volume of data,” specify “more than 1 terabyte of data processed per month.”
- Clearly define the units of measurement and the methods for calculating the metrics. For instance, “Number of API calls per day,” where an API call is precisely defined within the contract.
- Provide examples of usage scenarios and how they would be measured. This clarifies the intended application of the metrics and reduces the possibility of misinterpretation.
Incorporating a mechanism for auditing usage metrics is crucial. This involves:
- Regularly auditing usage data to ensure accuracy and identify any discrepancies.
- Establishing a clear process for resolving discrepancies, including the responsibilities of each party and the acceptable evidence for verifying usage.
- Defining a timeframe for the audit and the consequences of discrepancies.
Handling Disputes Related to Usage Calculations and Billing
A well-defined process for resolving billing disputes is essential for maintaining a positive business relationship.
A step-by-step process for resolving billing disputes could include:
- Initial contact between the licensee and the software provider to discuss the discrepancy.
- Joint review of the usage data and billing records to identify the source of the disagreement.
- Attempt to resolve the dispute through negotiation and mutual agreement.
- If negotiation fails, escalate the dispute to a designated contact person at each organization.
- If the dispute remains unresolved, utilize pre-agreed-upon dispute resolution mechanisms, such as mediation or arbitration.
- As a last resort, consider litigation.
Detailed record-keeping is crucial. This involves:
- Maintaining accurate and detailed records of usage data, including timestamps, user identifiers, and specific usage events.
- Storing billing information, including invoices, payment records, and any correspondence related to billing.
- Storing records in a secure and accessible format, with a defined retention period (e.g., seven years).
Examples of clauses to mitigate disputes:
In the event of a dispute regarding the accuracy of usage calculations, both parties agree to cooperate in good faith to reconcile the discrepancy using a mutually agreed-upon independent audit. If the discrepancy cannot be resolved within 30 days, the matter shall be submitted to binding arbitration under the rules of the American Arbitration Association.
If a system failure affects the accuracy of usage measurement, both parties will make reasonable efforts to estimate the usage based on available data and historical trends. Any significant discrepancies will be addressed through negotiation and a mutually agreed-upon adjustment to the billing.
Arbitration generally offers a faster and less expensive alternative to litigation, although enforceability can vary depending on jurisdiction. Litigation is more costly and time-consuming but offers a greater degree of enforceability.
Technical Implementation of Usage-Based Licensing: What Software Is Sold On Usage Based Theory
Implementing usage-based licensing requires a robust technical infrastructure capable of accurately tracking and monitoring software usage across diverse deployment models. This involves a complex interplay of hardware, software, and data management strategies, demanding careful planning and execution to ensure accuracy, scalability, and security.
Technical Infrastructure for Usage Tracking and Monitoring
Accurate usage tracking necessitates a well-defined technical infrastructure. The specific components will vary depending on the deployment model (on-premise, cloud, or hybrid), but key elements remain consistent. Scalability and fault tolerance are paramount, ensuring the system can handle increasing usage and withstand potential failures.
- Hardware: On-premise deployments require dedicated servers for application hosting, databases for storing usage data, and potentially load balancers for high availability. Cloud deployments leverage cloud provider resources (virtual machines, databases-as-a-service). Hardware considerations include processing power, memory, and storage capacity, scaled to meet anticipated usage levels. Examples include Amazon EC2 instances, Google Compute Engine, or Azure Virtual Machines for servers; and cloud-based database services such as Amazon RDS, Google Cloud SQL, or Azure SQL Database.
- Software Components: Monitoring agents reside within the software application, collecting usage data. Data pipelines process and transfer this data to a central database. These pipelines often employ message queues (e.g., Kafka, RabbitMQ) for asynchronous processing and improved scalability. Suitable database technologies include relational databases (PostgreSQL, MySQL) for structured data or NoSQL databases (MongoDB, Cassandra) for highly scalable, unstructured data.
The choice depends on the nature of the usage data and the expected volume.
- Scalability and Fault Tolerance: To ensure system reliability, a robust architecture is necessary. This includes techniques like load balancing, database replication, and automated failover mechanisms. Cloud-based solutions often provide built-in scalability features, automatically scaling resources based on demand. On-premise deployments require careful capacity planning and the implementation of redundant systems.
Step-by-Step Guide on Implementing Usage-Based Metering
This guide Artikels implementing usage-based metering in a Python application. The examples illustrate feature usage metering; similar approaches can be adapted for time-based and resource consumption metering.
- Step 1: Define Usage Metrics: Identify specific actions or features constituting usage. For example, a “feature_used” event could be triggered whenever a particular feature is accessed.
- Step 2: Implement Metering Logic: Use Python’s logging module or a dedicated metrics library (e.g., Prometheus client) to record usage events. Each event should include relevant metadata (timestamp, user ID, feature used).
- Step 3: Data Persistence: Store the collected metrics in a database (e.g., PostgreSQL). Use an appropriate ORM (Object-Relational Mapper) like SQLAlchemy for database interactions.
| Metering Method | Description | Implementation Details (Code Snippets) | Potential Challenges |
|---|---|---|---|
| Feature Usage | Tracks the number of times a specific feature is used | import logging; logger = logging.getLogger(__name__); logger.info('feature_used', extra='feature': 'report_generation', 'user_id': 123) | Handling concurrent access, preventing fraud through robust authentication and authorization. |
| Time-Based Usage | Tracks the duration of software usage | import time; start_time = time.time(); # ... application code ... end_time = time.time(); usage_duration = end_time - start_time; logger.info('usage_duration', extra='duration': usage_duration, 'user_id': 123) | Accurate time tracking across different time zones, handling system clock discrepancies. |
| Resource Consumption | Tracks CPU, memory, and disk usage | import psutil; cpu_percent = psutil.cpu_percent(interval=1); memory_info = psutil.virtual_memory(); disk_usage = psutil.disk_usage('/'); logger.info('resource_usage', extra='cpu': cpu_percent, 'memory': memory_info.percent, 'disk': disk_usage.percent, 'user_id': 123) | Efficient resource monitoring without significant overhead on application performance. |
Integration with Billing Systems
Integrating usage data with a billing system requires a structured approach. This example uses a hypothetical RESTful API; real-world APIs will vary.
- Data Formatting: Usage data is formatted as JSON payloads, containing user ID, usage metrics, and timestamps.
- API Calls: Python’s `requests` library makes API calls to the billing system. Error handling and retries are crucial for reliability.
- Security: API keys or OAuth 2.0 are used for authentication, and data is transmitted using HTTPS with encryption (TLS).
Consider the security implications of transmitting usage data to the billing system. Implement appropriate security measures such as encryption and authentication to protect sensitive data.
Data Storage and Reporting
A scalable and efficient data storage solution is vital. The choice of database technology depends on the volume and type of usage data.
- Database Selection: For high-volume, time-series data, a NoSQL database like TimescaleDB (built on PostgreSQL) is suitable. Relational databases are appropriate for smaller datasets or when complex queries are needed.
- Reporting: Reporting tools (e.g., Grafana, Kibana) can visualize usage data, providing insights into usage patterns and enabling efficient billing. Automated report generation (daily, weekly, monthly) can be implemented using scripting or scheduled tasks.
Testing and Validation
A comprehensive testing strategy ensures accuracy and reliability.
- Unit Testing: Test individual components (metering logic, data pipeline, API integration) in isolation.
- Integration Testing: Test the interaction between different components.
- System Testing: Test the entire system end-to-end, simulating real-world usage scenarios.
- Metrics: Measure accuracy (percentage of correctly recorded events), completeness (percentage of events captured), and latency (time taken to process events).
- Edge Cases: Test edge cases, such as concurrent access, network interruptions, and unexpected data formats.
Customer Perspective on Usage-Based Software

Usage-based software licensing presents a unique value proposition for customers, offering flexibility and cost optimization opportunities but also introducing potential complexities and risks. Understanding both the advantages and disadvantages is crucial for informed decision-making. This section examines the customer perspective, exploring the benefits and drawbacks, illustrating their impact with real-world examples, and outlining effective communication strategies for vendors.Advantages and Disadvantages of Usage-Based Software for CustomersUsage-based pricing models offer several key advantages for customers.
The most significant is the potential for cost savings. Customers only pay for the resources they consume, eliminating the need to purchase expensive, underutilized software licenses. This pay-as-you-go approach aligns expenditure with actual usage, leading to better budget control and predictable costs, especially for businesses with fluctuating workloads or seasonal demands. Furthermore, usage-based models often foster greater agility and scalability.
Many software companies are shifting towards usage-based pricing models, offering flexibility and scalability. This approach aligns with the philosophy of mindful consumption, much like the initiative championed by Choose Life Choose Words , which emphasizes responsible choices. Returning to software, this usage-based model often sees applications like cloud storage and SaaS platforms leading the charge, prioritizing value delivered over fixed licensing fees.
Customers can easily adjust their resource allocation based on project needs, scaling up or down as required without the constraints of fixed-term contracts or upfront license fees. This flexibility is particularly beneficial for startups and rapidly growing companies. However, usage-based models also present potential drawbacks. Unexpected spikes in usage can lead to unexpectedly high bills, requiring careful monitoring and proactive planning to avoid cost overruns.
The complexity of metering and billing can also lead to confusion and disputes regarding accurate usage tracking. Transparency and clear communication regarding pricing structures and usage metrics are therefore crucial for customer satisfaction. Finally, a dependence on a vendor’s metering system introduces a potential point of failure and can impact operational efficiency if the system malfunctions or is not adequately supported.
Case Studies Illustrating Impact on Customer Behavior and Adoption
A large e-commerce company transitioned from a perpetual license model to a usage-based model for its CRM software. Initially, the company experienced some apprehension due to concerns about potential cost overruns. However, by implementing robust monitoring and forecasting tools, they were able to effectively manage their usage and realized significant cost savings compared to their previous model. This success led to broader adoption of usage-based software across the company.
In contrast, a small marketing agency experienced challenges with a usage-based analytics platform due to a lack of clarity in the pricing structure and frequent billing discrepancies. This led to frustration and a negative perception of usage-based models, highlighting the importance of clear communication and robust billing systems. These case studies illustrate that successful adoption of usage-based software depends on factors such as effective usage monitoring, transparent pricing, and reliable vendor support.
Many software companies are shifting towards usage-based pricing models, charging based on actual consumption rather than upfront licensing. This approach is particularly relevant in educational settings, where resources are often limited. Consider, for example, the potential for a usage-based model applied to interactive educational tools like those found at Educational Word Searches , allowing schools to pay only for the number of student logins or completed activities.
This flexibility offers significant advantages for budgeting and resource allocation within the context of usage-based software sales.
Communicating the Value Proposition of Usage-Based Software to Potential Customers
Effective communication is crucial for overcoming customer apprehension and showcasing the benefits of usage-based software. Vendors should clearly articulate the cost savings potential through concrete examples and case studies, highlighting how the pay-as-you-go model aligns expenditure with actual usage. Emphasis should be placed on the flexibility and scalability of usage-based models, demonstrating how customers can easily adapt their resource allocation to meet changing demands.
Transparency is paramount. Vendors should provide clear and easily understandable explanations of the pricing structure, usage metrics, and billing processes. Proactive communication regarding potential cost fluctuations and strategies for managing usage is essential to build trust and mitigate customer concerns. Finally, strong customer support and reliable metering systems are critical for ensuring a positive customer experience and driving adoption.
A robust FAQ section addressing common customer concerns and providing detailed information on billing and usage monitoring can also significantly improve customer perception and trust.
Market Trends and Future Directions
The usage-based software licensing market is experiencing rapid evolution, driven by technological advancements and shifting business priorities. Understanding emerging trends, growth forecasts, and the impact of new technologies is crucial for businesses navigating this dynamic landscape. This section analyzes key market trends, forecasts future growth, examines the influence of AI and IoT, assesses the competitive landscape, and offers recommendations for businesses considering usage-based software.
Emerging Trends in Usage-Based Software
Several key trends are reshaping the usage-based software market, promising significant disruption in the coming years. These trends are primarily driven by technological advancements, evolving customer expectations, and a growing focus on operational efficiency.
| Trend | Driving Forces | Potential Impact |
|---|---|---|
| AI-powered Pricing Optimization: Dynamic pricing models leveraging AI to adjust prices based on real-time usage patterns and market conditions. Example: A SaaS provider adjusting subscription fees based on user activity and resource consumption. | Advancements in machine learning and AI, need for increased revenue predictability, growing data availability. | Increased revenue for software providers, more granular pricing that better reflects value for customers, potential for price discrimination concerns. |
| Micro-SaaS and Granular Usage Billing: Offering extremely specialized software functionalities as independent, usage-based services. Example: A marketing automation tool offering separate modules for email marketing, social media management, and analytics, each billed independently based on usage. | Increased demand for specialized tools, cloud computing infrastructure enabling flexible deployment, growing preference for modular software solutions. | Increased market accessibility for smaller developers, enhanced customer flexibility and control, potential for increased administrative overhead for both providers and customers. |
| Blockchain-based Usage Tracking and Licensing: Utilizing blockchain technology to ensure transparent and tamper-proof tracking of software usage and licensing agreements. Example: Securely recording and verifying software usage data on a distributed ledger to prevent unauthorized access or fraudulent activity. | Growing concerns about software piracy and licensing fraud, increasing trust in decentralized technologies, advancements in blockchain scalability and efficiency. | Enhanced security and trust in licensing agreements, reduced costs associated with licensing management, potential for increased complexity in implementation. |
| Serverless Computing and Usage-Based Pricing: Seamless integration of usage-based pricing with serverless architectures, allowing for automatic scaling and cost optimization. Example: A cloud-based application charging users only for the compute resources consumed during actual execution. | Increased adoption of serverless computing, desire for cost-effective solutions, demand for scalable and flexible infrastructure. | Reduced operational costs for businesses, improved scalability and efficiency, potential challenges in accurately predicting and managing costs. |
Growth Forecast for Usage-Based Software
Predicting the precise growth of usage-based software is challenging, but several market research firms offer projections. These forecasts are based on analyses of current market trends, technological advancements, and economic factors. It’s important to note that these are estimates and actual growth may vary.
(Note: A bar chart would be included here visualizing the CAGR for SaaS, Healthcare, and Manufacturing sectors from 2024-2028.
Due to limitations, I cannot generate images. The data for the chart would be sourced from reputable market research firms like Gartner, IDC, or Forrester. The chart would show the CAGR for each sector, with a legend clearly identifying each sector. Variations in growth rates would be explained by referencing industry-specific factors influencing adoption of usage-based models).
Impact of New Technologies on Usage-Based Software Licensing
AI and IoT are profoundly impacting usage-based software licensing, creating both opportunities and challenges.
- Opportunities: AI can enable dynamic pricing, personalized user experiences, and predictive maintenance. IoT devices can generate rich usage data for more accurate billing and improved service offerings.
- Challenges: AI algorithms require vast amounts of data, raising privacy and security concerns. The integration of IoT devices introduces complexities in data management, security, and billing. Accurate usage measurement in complex IoT environments can be technically challenging.
Competitive Landscape Analysis
Three major players in the usage-based software market demonstrate diverse strategies:
- Company A (Example: Salesforce): Focuses on enterprise SaaS solutions with tiered pricing models based on user numbers and features. Their strategy prioritizes comprehensive solutions and strong customer support.
- Company B (Example: Adobe): Employs a subscription model with various usage-based options for its creative software. Their strategy centers on offering flexible pricing plans to cater to diverse customer needs.
- Company C (Example: AWS): Offers a wide range of cloud services with granular usage-based pricing. Their strategy leverages the scalability and flexibility of cloud infrastructure to attract diverse customer segments.
Future Directions and Recommendations
Based on the analysis, here are three key recommendations for businesses considering usage-based software:
- Invest in data analytics capabilities: Accurate usage tracking and analysis are critical for successful implementation of usage-based pricing. This requires investment in robust data infrastructure and analytics tools.
- Prioritize data security and privacy: The collection and processing of usage data raise significant security and privacy concerns. Businesses must implement robust security measures and comply with relevant regulations.
- Develop flexible pricing models: Usage-based pricing should be tailored to specific customer needs and usage patterns. Offering various pricing tiers and options can enhance customer satisfaction and increase market competitiveness.
Examples of Usage-Based Software Companies
Numerous software companies have successfully adopted usage-based pricing models, demonstrating the viability and appeal of this approach for both vendors and consumers. This section provides concrete examples of such companies, highlighting their software types, pricing structures, and key features. The selection aims to represent a range of industries and software categories.
Examples of Usage-Based Software
The following table illustrates several companies that employ usage-based pricing for their software. The pricing models can be complex and often involve tiered structures or bundled services. The key features listed are not exhaustive but represent significant aspects of each software offering.
| Company Name | Software Type | Pricing Model | Key Features |
|---|---|---|---|
| Adobe | Creative Cloud (Photoshop, Illustrator, etc.) | Subscription based on individual apps or the entire suite; additional storage and features available at higher tiers. | Industry-standard tools for graphic design, video editing, and web development; cloud storage and collaboration features. |
| Salesforce | Customer Relationship Management (CRM) | Subscription based on the number of users, features accessed, and data storage; various editions cater to different business sizes. | Sales automation, marketing automation, customer service tools, analytics dashboards; customizable workflows and integrations. |
| Twilio | Communications Platform as a Service (CPaaS) | Pay-as-you-go model based on the number of messages, calls, and other communication events processed. | APIs for SMS, voice, video, and chat; global reach and scalability; integration with various development platforms. |
| AWS (Amazon Web Services) | Cloud Computing Services | Pay-as-you-go model based on compute time, storage used, data transfer, and other resources consumed. | Wide range of services including compute, storage, databases, networking, and machine learning; scalability and global infrastructure. |
| Stripe | Payment Processing Platform | Transaction-based fees; percentage of each transaction processed plus potential fixed fees for certain features. | Secure and reliable payment processing; support for multiple payment methods; fraud prevention tools; developer-friendly APIs. |
Security and Privacy Considerations
Usage-based software, by its nature, necessitates the collection and processing of user data to determine licensing fees. This inherent characteristic introduces significant security and privacy challenges that must be proactively addressed to maintain user trust and comply with relevant regulations. Failure to implement robust security measures can lead to substantial financial losses, reputational damage, and legal repercussions.
Data Security Implications
The collection and storage of usage data present several security risks. Data breaches, resulting from vulnerabilities such as SQL injection or cross-site scripting (XSS), can expose sensitive information about users and their activities. SQL injection attacks exploit vulnerabilities in database queries to gain unauthorized access to data. For instance, a malicious actor might inject SQL code into an input field to retrieve all user data from a database.
XSS attacks, on the other hand, involve injecting malicious scripts into websites to steal user cookies or other sensitive information. Mitigation strategies include input validation and sanitization to prevent SQL injection, and robust output encoding to prevent XSS attacks. Furthermore, employing a web application firewall (WAF) can provide an additional layer of protection. The choice of storage method—cloud-based or on-premise—also impacts security.
Cloud storage providers typically offer advanced security features, but reliance on third-party security necessitates careful vendor selection and contract negotiation. On-premise solutions offer greater control but require significant investment in infrastructure and security expertise. Regular security audits and penetration testing are crucial for identifying and addressing vulnerabilities in both scenarios.
User Data Privacy
Protecting user privacy in usage-based software requires a multi-faceted approach. Data minimization, collecting only the data strictly necessary for billing and service delivery, is paramount. Techniques like anonymization and pseudonymization can further enhance privacy by removing or replacing personally identifiable information (PII). Anonymization involves rendering data completely unidentifiable, while pseudonymization replaces PII with pseudonyms, allowing data analysis while preserving user privacy.
Access control mechanisms should restrict data access to authorized personnel only, employing role-based access control (RBAC) to limit access based on job responsibilities. Data encryption, both in transit (using HTTPS) and at rest (using encryption at the database level), is essential to protect data from unauthorized access.
Data Protection Compliance
Adherence to data protection regulations like GDPR, CCPA, and HIPAA is crucial. The table below summarizes key requirements:
| Regulation | Consent Mechanism | Data Subject Rights | Breach Notification | Data Minimization |
|---|---|---|---|---|
| GDPR | Informed consent, explicit consent, legitimate interest | Right to access, rectification, erasure, restriction of processing, data portability, objection | Notification within 72 hours | Only collect necessary data |
| CCPA | Opt-in consent, opt-out consent | Right to access, delete, and know | Notification as required by law | Only collect necessary data |
| HIPAA | Authorization, business associate agreements | Individual rights to access, amend, and request restrictions | Notification as required by law | Minimum Necessary Standard |
Security Auditing and Monitoring
A comprehensive security plan should include regular security audits and penetration testing conducted by independent security experts. These assessments identify vulnerabilities and weaknesses in the system’s security posture. Security Information and Event Management (SIEM) systems provide real-time monitoring and threat detection capabilities. These systems collect and analyze security logs from various sources to identify suspicious activities and potential security breaches.
Detailed logging and reporting mechanisms are necessary to track security events and maintain an audit trail for compliance and incident investigation.
Many software companies are shifting towards usage-based pricing models, charging based on actual consumption rather than upfront licensing. This approach is particularly relevant when considering the complexities of managing access and utilization, a challenge often addressed by robust knowledge bases like the one found at lighthouse knowledge base , which itself could benefit from a usage-based support model.
Ultimately, the success of usage-based software hinges on transparent and accessible information for users, mirroring the need for effective knowledge base management.
Data Retention Policy
A clear data retention policy is essential, outlining the duration of data storage and the criteria for deletion. The policy should specify the methods for securely deleting data, ensuring its irretrievability. This often involves multiple stages of deletion, including physical destruction of storage media where appropriate, and should align with legal and regulatory requirements, such as data retention mandates imposed by specific jurisdictions or industry standards.
Incident Response Plan
A comprehensive incident response plan Artikels procedures for handling data breaches or security incidents. This plan should detail the steps for containment, eradication (removing the threat), recovery (restoring systems and data), and post-incident analysis (to identify root causes and prevent future incidents). Clearly defined roles and responsibilities for each team member are crucial for efficient incident response. Regular drills and simulations help ensure the plan’s effectiveness.
Scalability and Performance
Usage-based software licensing presents unique scalability and performance challenges due to the dynamic nature of pricing and the need for real-time metering and billing. Efficiently handling a large number of users and transactions while maintaining low latency is crucial for user satisfaction and business viability. This section details the challenges and strategies for optimizing the performance and scalability of usage-based software systems.
Scalability Challenges in Usage-Based Software
Scaling a usage-based software system to handle a large number of concurrent users (e.g., 100,000) and a high transaction volume (e.g., 10,000 transactions per second) requires careful consideration of potential bottlenecks. These bottlenecks can arise at various points in the system architecture, impacting responsiveness and overall system performance.
- Database Bottlenecks: High transaction volumes can overwhelm a relational database, leading to slow query response times and reduced throughput. The inherent limitations of relational database schema in handling highly variable usage data might lead to performance degradation. For instance, storing detailed usage records for 100,000 concurrent users performing 10,000 transactions per second requires significant database resources and efficient query optimization.
Many software companies are shifting towards usage-based pricing models, offering flexibility and scalability. A prime example of this approach is evident in the innovative solutions provided by Techsquiral , which demonstrates how this model can be successfully implemented. This trend highlights a broader movement towards software solutions where the cost directly reflects the actual utilization, leading to more predictable and efficient budgeting for businesses.
NoSQL databases, on the other hand, offer better scalability for handling large volumes of unstructured or semi-structured data but might lack the transactional consistency of relational databases.
- Metering Infrastructure Bottlenecks: The metering infrastructure itself, responsible for capturing and processing usage data, can become a bottleneck. High-volume data ingestion, real-time processing, and storage requirements can strain resources, leading to delays in billing and inaccurate usage reports. For example, if the system relies on a single point of ingestion, a surge in usage data could cause delays and data loss.
- API Bottlenecks: The APIs used for communication between the software application and the metering system can become saturated under heavy load. Inefficient API design or lack of proper load balancing can lead to slow response times and errors. Consider an API that is not designed for concurrency. This could lead to slow response times or failures under high user load.
The choice of database technology significantly impacts scalability. Relational databases (e.g., PostgreSQL, MySQL) excel in transactional consistency and data integrity but can struggle with high-volume, unstructured data. NoSQL databases (e.g., MongoDB, Cassandra) offer better horizontal scalability and flexibility but might require more complex data modeling and management. Under high load, NoSQL databases generally demonstrate superior performance in terms of write throughput and scalability, while relational databases may exhibit better performance for complex transactional operations requiring data integrity.Scaling the metering infrastructure necessitates a distributed architecture.
Many software solutions, like cloud storage or CRM systems, operate on a usage-based pricing model. This contrasts sharply with traditional licensing. Think about how access to resources is managed, much like the distribution of benefits, for instance, the eligibility criteria for programs such as Food Stamps , which are carefully controlled based on need. Returning to software, this usage-based approach allows for flexible scaling and cost optimization, mirroring the dynamic nature of resource allocation in social programs.
This involves distributing the workload across multiple servers or cloud instances, enabling horizontal scalability. Solutions include using message queues (e.g., Kafka, RabbitMQ) for asynchronous processing of usage data and employing distributed data storage solutions (e.g., Hadoop Distributed File System (HDFS), cloud storage services).
Optimizing Performance of Usage-Based Metering and Billing
Optimizing the performance of usage-based metering and billing systems focuses on minimizing latency and maximizing throughput. This involves employing various optimization techniques at each stage of the process: metering, aggregation, and billing.
- Metering Optimization: Efficient metering involves minimizing the overhead of data collection. Techniques include asynchronous metering, batch processing of usage data, and using lightweight metering agents. For example, instead of sending usage data to the billing system in real-time, data could be aggregated and sent periodically.
- Aggregation Optimization: Efficient aggregation involves reducing the amount of data processed. Techniques include using pre-aggregated data, employing efficient data structures, and optimizing aggregation queries. For example, instead of processing individual usage events, they could be aggregated at regular intervals.
- Billing Optimization: Efficient billing involves optimizing the billing process itself. Techniques include using caching, asynchronous billing, and parallel processing of billing tasks. For example, caching frequently accessed customer data can significantly reduce the time it takes to generate invoices.
| Caching Strategy | Pros | Cons | Performance Implications |
|---|---|---|---|
| In-Memory Cache | Low latency, high throughput | Limited capacity, data loss on restart | Excellent for frequently accessed data |
| Distributed Cache | Scalable, high availability | Higher latency, more complex management | Suitable for large datasets and high traffic |
| Redis | Fast, in-memory data structure store, versatile | Requires careful management of data persistence | Excellent for session management, caching frequently accessed data |
| Memcached | Simple, fast, distributed in-memory caching | Limited data structures, no persistence | High performance for simple caching needs |
A performance testing plan should include various metrics and tools. Metrics to be measured include latency (response time), throughput (transactions per second), error rate, and resource utilization (CPU, memory, network). Tools like JMeter and k6 can be used to simulate high user load and measure system performance under stress. The plan should cover various load scenarios, including peak loads and failure scenarios.
This data will allow for informed decision-making regarding system architecture and resource allocation.
Impact of Usage-Based Licensing on Software Architecture and Design
Usage-based licensing significantly influences software architecture and design. Robust metering capabilities are essential, requiring careful consideration of modularity and maintainability. The choice of architectural patterns and technology stack is also directly impacted.Microservices architecture offers better scalability and flexibility for usage-based systems by enabling independent scaling of different components. An event-driven architecture can facilitate efficient processing of usage data by decoupling different parts of the system.
The technology stack should be chosen to support the specific requirements of the system, including high throughput, low latency, and scalability. For instance, using a language like Go for its concurrency features and a NoSQL database for its scalability could be beneficial.Security is paramount in usage-based licensing. Secure metering and billing processes are necessary to prevent fraud and unauthorized access.
Security best practices include data encryption, secure authentication and authorization, and regular security audits. Implementing robust logging and monitoring mechanisms can help detect and respond to security incidents.
Integration with Other Systems
Successful integration of usage-based software with existing enterprise systems is crucial for maximizing its value and avoiding operational silos. Effective integration allows for seamless data flow, automated processes, and a unified view of customer usage and billing. This section details the challenges, solutions, and best practices for integrating usage-based software with various enterprise systems.
Challenge & Solution Matrix for CRM and ERP Integration
Integrating usage-based software with CRM and ERP systems presents several challenges. Addressing these requires a strategic approach encompassing data transformation, security protocols, and robust error handling. The following matrix Artikels common challenges and potential solutions, along with feasibility and cost assessments.
| Challenge | Solution | Feasibility | Cost |
|---|---|---|---|
| Data Format Discrepancies | 1. Develop custom ETL processes. 2. Utilize data mapping tools. 3. Employ API transformations. | High | Medium to High |
| Security Concerns | 1. Implement robust authentication (OAuth 2.0, JWT). 2. Encrypt data in transit and at rest. 3. Regularly audit access controls. | High | Medium |
| Real-time Data Synchronization | 1. Utilize real-time APIs (WebSockets, Server-Sent Events). 2. Implement change data capture (CDC). 3. Employ message queues (Kafka, RabbitMQ). | Medium to High | Medium to High |
| Data Volume and Velocity | 1. Implement data warehousing and aggregation. 2. Utilize distributed databases. 3. Employ data streaming technologies. | Medium to High | High |
| Lack of Standardized APIs | 1. Develop custom connectors. 2. Use middleware solutions (MuleSoft, IBM Integration Bus). 3. Employ API gateways for abstraction. | Medium | Medium to High |
Successful Integration Case Studies
Three case studies illustrate successful integration of usage-based software with enterprise systems.
- Case Study 1 (CRM): A SaaS company offering a usage-based project management tool integrated with Salesforce CRM using Salesforce’s API. The integration allowed for automated lead scoring based on user engagement within the project management tool, resulting in a 15% increase in qualified leads and a 10% increase in sales conversion rates. Key metrics included improved lead qualification accuracy and reduced sales cycle length.
The integration method was API-based, leveraging Salesforce’s RESTful API.
- Case Study 2 (ERP): A manufacturing company using a usage-based machine monitoring system integrated with its SAP ERP system via custom middleware. This integration enabled real-time tracking of machine performance, allowing for predictive maintenance and optimized production scheduling. The result was a 20% reduction in downtime and a 5% increase in overall production efficiency. Key metrics included reduced machine downtime, improved production scheduling accuracy, and decreased maintenance costs.
- Case Study 3 (Billing System): A cloud storage provider integrated its usage-based storage service with a third-party billing system using an ETL process. This integration automated billing processes, improving accuracy and reducing manual effort. The integration resulted in a 95% reduction in billing errors and a 10% reduction in billing processing time. Key metrics included improved billing accuracy, reduced processing time, and minimized manual intervention.
API Design Impact Analysis
The choice of API design significantly impacts integration ease and performance. RESTful APIs offer simplicity and broad adoption, while GraphQL allows for precise data retrieval. Synchronous APIs provide immediate responses, but asynchronous APIs offer better scalability.
- RESTful API (Python Example): Retrieving user usage data:
import requests
response = requests.get('https://api.example.com/usage?user_id=123')
data = response.json()
- GraphQL API (JavaScript Example): Updating billing information:
const query = `
mutation UpdateBilling($userId: ID!, $amount: Float!)
updateBilling(userId: $userId, amount: $amount)
success`;
const variables = userId: '123', amount: 100.00 ;
| API Design | Advantages | Disadvantages |
|---|---|---|
| RESTful | Simple, widely adopted, well-documented | Can be inefficient for complex data retrieval |
| GraphQL | Efficient data fetching, client-specified data | Steeper learning curve, requires a GraphQL server |
| Synchronous | Immediate response, simple to implement | Can block requests, scalability limitations |
| Asynchronous | High scalability, improved responsiveness | More complex implementation, requires handling callbacks or promises |
Security Considerations in Integration
Securing the integration requires robust authentication, data encryption, and access control.
- Authentication Methods: OAuth 2.0, JWT, API keys.
- Data Encryption: TLS/SSL for data in transit, AES encryption for data at rest.
- Access Control: Role-based access control (RBAC), least privilege principle.
Data Transformation Requirements
Integrating usage-based data requires transforming data to match the target system’s structure.
- Data Type Conversions: Converting data types between systems (e.g., string to integer).
- Data Cleansing: Handling missing or inconsistent data.
- Data Normalization: Structuring data to reduce redundancy.
Scalability and Performance of Integration
Strategies for ensuring scalability and performance include database optimization, caching, and load balancing.
- Database Design: Choosing appropriate database technologies (e.g., NoSQL for high volume data).
- Caching Mechanisms: Caching frequently accessed data to reduce database load.
- Load Balancing: Distributing traffic across multiple servers.
Error Handling and Monitoring
A robust error handling and monitoring strategy is essential for reliable integration.
- Error Detection and Logging: Implementing comprehensive logging and exception handling.
- Error Resolution: Establishing procedures for identifying and resolving integration errors.
- Performance Monitoring: Utilizing monitoring tools to track integration performance.
Cost-Benefit Analysis Framework
A cost-benefit analysis should consider development, maintenance, infrastructure costs, and benefits like improved efficiency, reduced costs, and increased revenue. The framework should include detailed estimations for each cost and benefit component, allowing for a comprehensive evaluation of different integration strategies. Sensitivity analysis should be incorporated to account for uncertainty in cost and benefit estimations. A discounted cash flow (DCF) analysis can be used to determine the net present value (NPV) of each integration strategy.
Support and Maintenance
Effective support and maintenance are crucial for the success of usage-based software. The nature of usage-based licensing, with its variable costs and reliance on accurate metering, necessitates robust support structures and proactive strategies to ensure customer satisfaction and minimize disruptions. This section details various support models, addresses challenges specific to usage-based software, and emphasizes the importance of clear documentation and proactive support.
Support Models for Usage-Based Software
Different support models cater to varying customer needs and budgets. Tiered support structures, on-demand support, and proactive support are common approaches, each offering different levels of service and response times. Service Level Agreements (SLAs) define the expected performance of each model.
| Support Model | Response Time (SLA) | Support Channels | Expertise Level | Cost |
|---|---|---|---|---|
| Bronze | >24 hours | Email only | Basic technical support; access to a knowledge base and FAQs. | Low |
| Silver | <8 hours | Email, Chat | Intermediate technical support; access to a knowledge base, FAQs, and phone support during business hours. | Medium |
| Gold | <1 hour | Phone, Email, Chat, Dedicated Account Manager | Advanced technical support; 24/7 phone and chat support, proactive monitoring, and a dedicated account manager. | High |
Challenges of Providing Effective Support for Usage-Based Software
Providing effective support for usage-based software presents unique challenges. These stem from the complexities of metering, fluctuating usage patterns, diverse user skill levels, and the need for secure data handling.
- Metering accuracy and disputes regarding usage charges: Discrepancies can arise from inaccurate metering, system errors, or misunderstandings of pricing models. Resolution strategies involve robust auditing processes, clear usage reporting, and dispute resolution mechanisms. For example, a discrepancy might arise if a user is charged for processing power exceeding their allocated quota, due to a spike in unexpected activity or a software bug. Thorough investigation and potentially pro-rata adjustments can resolve such issues.
- Managing fluctuating support demands based on usage patterns: Usage-based software often experiences peak demand periods. Strategies for scaling support resources include employing flexible staffing models, utilizing automated support tools (e.g., chatbots), and leveraging external support providers during peak times.
- Providing support for a diverse user base with varying technical skills: Support should be tailored to different skill levels. This includes providing various documentation formats (e.g., visual guides, video tutorials), offering multiple support channels, and creating tiered support options that match user expertise.
- Maintaining data security and privacy during support interactions: Secure remote access protocols (e.g., VPNs, encrypted connections) and strict data handling policies are essential to protect sensitive information during support interactions. Regular security audits and employee training are crucial.
- Integrating support processes with billing and usage monitoring systems: Seamless data flow between support, billing, and usage monitoring systems is critical for efficient problem resolution and accurate billing. Integration allows for quick access to usage data during support interactions, enabling faster troubleshooting and dispute resolution.
Importance of Clear Documentation and User Training
Comprehensive documentation and user training are paramount in reducing support tickets and improving user satisfaction. These resources empower users to resolve issues independently and maximize software utilization.
- Effective user manuals and FAQs: These should be well-structured, using clear and concise language, visuals (e.g., screenshots, diagrams), and tutorials. A logical flow of information, with readily accessible troubleshooting sections, is essential. For example, a well-designed manual might include interactive tutorials demonstrating common tasks, with clear explanations and step-by-step instructions.
- Comprehensive user training programs: Online tutorials, webinars, and in-person workshops can cater to different learning styles and user groups. The choice of delivery method should consider the user’s technical proficiency and learning preferences.
- Knowledge base or help center: An easily accessible knowledge base with robust search functionality, clear categorization, and regular updates empowers users to find solutions quickly. Features like tagging, rating systems, and community forums can further enhance usability.
- Proactive communication: Newsletters, announcements, and release notes keep users informed about updates, new features, and best practices, reducing the likelihood of support requests stemming from a lack of information.
Best Practice: Prioritize self-service support options through comprehensive documentation and a robust knowledge base to reduce the burden on support staff and improve user independence.
Proactive Support Strategies
Proactive support minimizes support requests by addressing potential issues before they escalate.
- Predictive Monitoring and Alerting: Analyzing usage patterns to identify potential issues (e.g., approaching quota limits, resource bottlenecks) and proactively alerting users allows for timely intervention, preventing service disruptions. For example, the system could send an email notification when a user’s usage approaches 80% of their allocated quota.
- Regular System Health Checks and Performance Tuning: Automated system health checks identify and address performance issues before they impact users. Proactive performance tuning optimizes resource allocation, preventing bottlenecks and improving overall system stability. This might involve automatically adjusting server resources based on predicted usage spikes.
- Personalized Onboarding and Guidance: Tailored onboarding processes, providing users with relevant training and support based on their specific needs and usage patterns, improve initial adoption and reduce early-stage support requests. This could involve a series of guided tutorials, tailored to the user’s role and industry.
Illustrative Example: A Cloud Storage Service
This section details a hypothetical cloud storage service, “CloudStore,” employing a usage-based pricing model. The service is designed to cater to a diverse range of users, from individuals needing basic storage to businesses requiring robust solutions with advanced features. The pricing structure directly reflects the resources consumed, promoting efficient resource utilization and transparent cost management.CloudStore offers three distinct storage tiers, each with varying features and pricing.
These tiers are designed to accommodate different user needs and budgets, ensuring a flexible and scalable solution. Usage is tracked meticulously to ensure accurate billing and resource allocation.
Storage Tiers and Pricing
CloudStore’s pricing is based on the amount of storage used, the number of files stored, and the level of access control features selected. The three tiers are: Basic, Pro, and Enterprise.
| Tier | Storage Capacity (GB) | File Count Limit | Data Transfer (GB/month) | Access Control | Price/GB/Month |
|---|---|---|---|---|---|
| Basic | 100 | 10,000 | 100 | Basic User Permissions | $0.05 |
| Pro | 500 | 100,000 | 500 | Granular User and Group Permissions, Versioning | $0.03 |
| Enterprise | Unlimited | Unlimited | Unlimited | Advanced Access Control, Role-Based Access Control (RBAC), Auditing | $0.01 |
Additional charges apply for exceeding the included data transfer allowance in each tier. Overages are billed at $0.10 per GB. There are no setup fees.
Usage Tracking Mechanisms
CloudStore employs a robust system for tracking storage usage and data transfer. This system continuously monitors storage consumption at the user level, accurately recording the amount of data stored and the volume of data transferred. The system leverages distributed databases and real-time monitoring tools to ensure accurate and up-to-date usage metrics. Daily summaries of usage are provided to users through a dedicated dashboard, allowing for proactive monitoring and cost management.
Billing is conducted monthly based on the accumulated usage data.
Data Security and Privacy
Data security and user privacy are paramount. CloudStore utilizes industry-standard encryption techniques both in transit and at rest to protect user data. Data centers are secured with multiple layers of physical and cybersecurity measures. Compliance with relevant data privacy regulations, such as GDPR and CCPA, is ensured through robust data governance policies and procedures. Regular security audits and penetration testing are conducted to identify and address potential vulnerabilities.
Users retain full ownership and control over their data.
Scalability and Performance
CloudStore is built on a highly scalable and distributed infrastructure. The system can easily accommodate increasing user demand and data volumes. Performance is optimized through the use of advanced caching mechanisms, content delivery networks (CDNs), and load balancing techniques. This ensures fast and reliable access to stored data, even during peak usage periods. The system is designed to handle millions of users and petabytes of data.
Amazon S3 and Google Cloud Storage are examples of existing services with similar scalability.
Frequently Asked Questions
What are some examples of ambiguous usage metrics?
Examples include vaguely defined terms like “active user,” “significant usage,” or “substantial data volume.” These lack precise, quantifiable definitions, leading to potential disputes.
How can data privacy be ensured in usage-based software?
Data privacy is paramount. Employ anonymization and pseudonymization techniques, minimize data collection, implement robust access controls, and utilize encryption both in transit and at rest. Compliance with regulations like GDPR and CCPA is essential.
What are the security implications of collecting usage data?
Collecting usage data introduces security risks. Potential vulnerabilities include SQL injection and cross-site scripting. Mitigation strategies involve secure coding practices, input validation, and regular security audits and penetration testing.
How can disputes regarding usage calculations be resolved?
Establish a clear dispute resolution process in the contract, outlining steps for reconciliation, escalation procedures, and potential arbitration or mediation. Maintain detailed records of usage data and billing information.


