Samsara Knowledge Base: Dive into the heart of this dynamic system! Imagine a vast repository of interconnected data, a digital tapestry woven from sensor readings, vehicle diagnostics, and driver logs. This isn’t just a database; it’s a living, breathing ecosystem that fuels critical decision-making and operational efficiency. We’ll explore its intricate architecture, delve into its powerful querying capabilities, and uncover the secrets behind its robust security measures.
Get ready for a journey into the world of Samsara’s data powerhouse.
This exploration will cover the Samsara Knowledge Base’s design, from its underlying database structure and data types to its sophisticated data retrieval and security protocols. We’ll examine real-world scenarios, highlighting how data is integrated, queried, and visualized to deliver actionable insights. We’ll also discuss future enhancements, ensuring you have a complete understanding of this vital system’s capabilities and potential.
Data Integration with Samsara
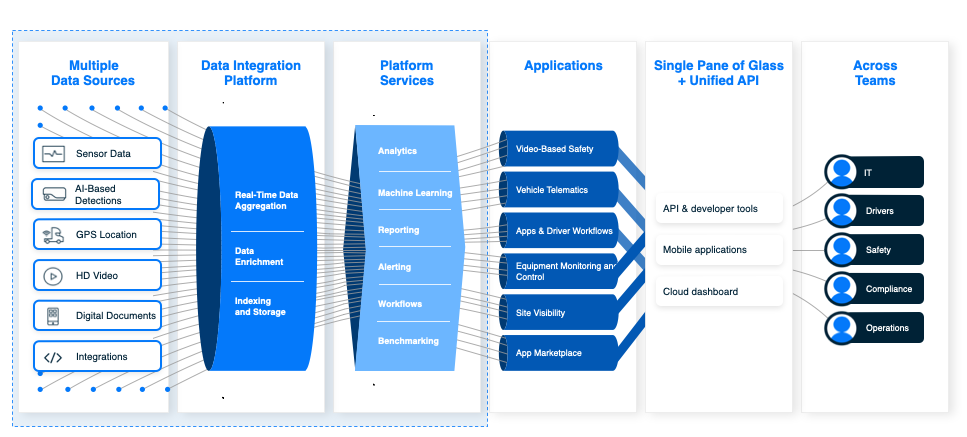
Unlocking the true potential of Samsara lies in seamlessly integrating its robust platform with external data sources. This allows for a richer, more contextualized understanding of your operations, leading to improved decision-making and enhanced efficiency. By connecting disparate systems, you create a unified view of your business, fostering a holistic and insightful perspective. This section delves into the practical aspects of integrating external data with Samsara, exploring various methods, challenges, and best practices.
Data Source Examples & Integration Methods
Integrating diverse data sources significantly expands Samsara’s capabilities. Strategic integration unlocks powerful analytics and allows for more informed operational strategies. The following examples illustrate the potential.
- Weather API (e.g., OpenWeatherMap): This API provides real-time weather data in JSON format. Integration can be achieved through API calls, fetching relevant data such as temperature, humidity, and precipitation. Integrating this data allows for contextualizing vehicle performance and driver behavior based on weather conditions. Key data fields include temperature, precipitation type, and wind speed. This allows for analysis of how weather impacts fuel consumption, route optimization, and potential safety hazards.
- Manufacturing ERP System (e.g., SAP): An ERP system typically provides data in XML or CSV format. An ETL (Extract, Transform, Load) process would be ideal for integrating data from an ERP system. This would involve extracting relevant data, transforming it into a suitable format, and loading it into Samsara. Valuable data fields include production schedules, inventory levels, and equipment maintenance records.
Linking this data to Samsara’s vehicle tracking enables optimization of logistics and delivery scheduling, directly correlating production output with transportation efficiency.
- Third-Party Fleet Management Software (e.g., a telematics provider): Data exchange with other fleet management systems might utilize APIs or data files (CSV, JSON). API calls offer real-time integration, while file transfers can handle batch updates. Integrating data from a third-party system could provide additional context for vehicle diagnostics and driver behavior. Valuable data fields include driver scores, vehicle diagnostics codes, and maintenance alerts. Combining this data within Samsara provides a comprehensive view of fleet health and driver performance, facilitating proactive maintenance and driver training programs.
Challenges and Best Practices
Integrating external data sources presents inherent challenges. Proactive planning and implementation of best practices are crucial to mitigate potential risks and ensure a successful integration.
| Challenge | Best Practice 1 | Best Practice 2 |
|---|---|---|
| Data Format Inconsistencies | Establish clear data mapping and transformation rules upfront, utilizing standardized formats like JSON whenever possible. | Implement robust data validation and cleansing procedures to handle inconsistencies and missing values. |
| Data Security Concerns | Employ secure communication protocols (HTTPS, TLS) and implement appropriate authentication and authorization mechanisms. | Encrypt sensitive data both in transit and at rest, complying with relevant regulations like GDPR and CCPA. |
| Real-time Data Synchronization | Utilize real-time data streaming technologies (e.g., Kafka, WebSockets) for applications requiring immediate updates. | Implement change data capture (CDC) mechanisms to efficiently track and synchronize only the changes in the data sources. |
Workflow Design: Hypothetical Sensor Network Integration
Integrating a sensor network requires a structured approach. This example Artikels a workflow for a hypothetical sensor network measuring temperature, humidity, and pressure.
- Data Acquisition: The sensor network communicates using MQTT (Message Queuing Telemetry Transport), a lightweight publish-subscribe protocol ideal for IoT devices. Sensors transmit data packets containing timestamps, temperature, humidity, and pressure readings.
- Data Preprocessing and Cleaning: Data is preprocessed using a data ingestion pipeline. This pipeline identifies and handles outliers (e.g., temperature readings outside a reasonable range) using statistical methods (e.g., Z-score). Missing values are imputed using techniques such as linear interpolation or mean imputation.
- Data Transformation: The preprocessed data is transformed into JSON format, aligning with Samsara’s API requirements. This includes creating a structured JSON schema with clear field names and data types.
- Data Loading: The transformed JSON data is loaded into Samsara using its API, specifically targeting a custom-created data table within the Samsara knowledge base dedicated to environmental sensor data.
- Data Validation and Error Handling: Data validation checks are implemented at each stage to ensure data integrity. Error handling mechanisms, such as logging and alerting, are in place to identify and address integration issues.
Data Governance and Security
A comprehensive data governance plan is essential. This plan Artikels procedures for data access control, using role-based access control (RBAC) to restrict access to sensitive data based on user roles. Data encryption (both in transit and at rest) protects against unauthorized access. Compliance with regulations such as GDPR and CCPA is ensured through data anonymization and consent management processes.
A clear incident response plan is in place to address data breaches, including procedures for notification, investigation, remediation, and post-incident review.
Scalability and Maintainability, Samsara knowledge base
The chosen integration methods should be scalable. API-based integrations and data streaming allow for easy scaling to accommodate increasing data volumes. ETL processes can be parallelized to improve performance. A robust maintenance plan includes regular monitoring of data quality using dashboards and alerts. Troubleshooting procedures, documentation, and version control ensure smooth operation.
Automated testing and continuous integration/continuous deployment (CI/CD) pipelines streamline updates and reduce downtime. Monitoring tools such as Grafana and Prometheus can track key metrics like data latency and integration errors, providing insights into system health and performance.
User Access and Permissions
The Samsara knowledge base is designed with a robust system of user access and permissions to ensure data security and integrity while facilitating collaboration. This system employs a multi-layered approach, combining role-based access control with strong authentication and encryption measures, mirroring the principles of mindful stewardship over valuable information. Understanding these mechanisms is crucial for both efficient knowledge sharing and maintaining the sanctity of the information contained within.
User Roles and Permissions
The Samsara knowledge base utilizes a tiered system of user roles, each with specific permissions. This approach ensures that only authorized individuals can access and modify sensitive information, promoting responsibility and accountability. The granular control offered allows for precise management of access rights based on individual needs and responsibilities.
- Administrator: Possesses full access to all aspects of the knowledge base, including managing users, articles, categories, and system settings. They can view, edit, create, and delete any article, manage all user accounts, and control access to all sections.
- Editor: Can view, edit, create, and delete articles within assigned categories or sections. They cannot manage user accounts or access system settings. For example, an editor might manage the “Technical Support” section but lack access to the “Internal Communications” section.
- Contributor: Can create and edit articles within assigned categories or sections, but cannot delete articles. They lack access to user management and system settings. A contributor might be responsible for drafting new articles for a specific product line.
- Viewer: Can only view articles within assigned categories or sections. They have no editing or management capabilities. Viewers might be external partners with limited access to specific documentation.
- Guest: Has access to a limited, pre-defined set of public articles. They cannot access internal documentation or create/edit content. This role is ideal for external clients or customers needing access to specific FAQs.
Security Measures
Protecting the integrity and confidentiality of information within the Samsara knowledge base is paramount. We employ a comprehensive suite of security measures to mitigate risks and safeguard data. This commitment reflects our dedication to transparency and trust.
- Authentication: Multi-factor authentication (MFA) is mandatory for all users, requiring a combination of password and a second factor (e.g., one-time code from an authenticator app). Strong password complexity requirements are enforced.
- Authorization: Role-based access control (RBAC) governs access to resources. Each user’s permissions are strictly defined by their assigned role, limiting access to only necessary information.
- Data Encryption: Data is encrypted both in transit (using HTTPS) and at rest (using AES-256 encryption). This ensures that data remains confidential even if a breach occurs.
- Security Audits and Penetration Testing: Regular security audits and penetration testing are conducted to identify and address vulnerabilities proactively. These assessments are performed by certified security professionals.
- Incident Response Plan: A detailed incident response plan is in place to handle security incidents efficiently and effectively, minimizing potential damage and ensuring swift recovery.
User Roles, Permissions, and Access Levels
| Role Name | Description of Role | Permissions | Access Level |
|---|---|---|---|
| Administrator | Full control over the knowledge base | View Edit Create Delete Articles Manage Users Access all sections | Full Access |
| Editor | Edits and creates articles within assigned sections | View Edit Create Delete Articles (within assigned sections) | Limited Access |
| Contributor | Creates articles within assigned sections | View Create Edit Articles (within assigned sections) | Limited Access |
| Viewer | Views articles within assigned sections | View Articles (within assigned sections) | Read-Only |
| Guest | Access to public articles only | View Public Articles | Read-Only |
User Authentication and Authorization Process
The authentication process begins with the user entering their credentials (username and password). The system verifies these credentials against the database. If successful, the system then checks the user’s role and associated permissions. Based on the role, the system grants or denies access to specific resources within the knowledge base. This authorization is dynamic, adjusting in real-time based on changes to user roles and permissions. Any failed attempts are logged for security monitoring.
Access Request Process
To request access to the Samsara knowledge base, submit a request through the designated online form, providing your name, department, required access level, and a brief justification for access. The request is reviewed by the designated administrator within 2 business days. Notification of approval or rejection is sent via email. Contact the IT helpdesk at [email protected] for assistance.
User Account Management
Only administrators can create, modify, and delete user accounts and reset passwords. All actions are logged and audited for accountability. This includes detailed records of account creation, modification, deletion, and password resets, providing a complete audit trail.
Access Revocation Process
Administrators can revoke access to the knowledge base for specific users or roles. The system immediately disables access upon revocation, and a notification email is sent to the affected user explaining the reason for the revocation. All revocation actions are logged and audited, maintaining a clear record of access changes.
Unauthorized Access Prevention
The Samsara knowledge base employs intrusion detection and prevention systems (IDPS) to monitor network traffic and identify malicious activity. These systems provide real-time alerts and automatically block suspicious attempts to access the system. Comprehensive monitoring and alerting systems are in place, providing immediate notifications of potential security breaches.
Security Best Practices
The Samsara knowledge base adheres to industry best practices for data security and access control, aligning with standards such as ISO 27001 and the NIST Cybersecurity Framework. Regular security assessments and compliance reviews ensure the ongoing effectiveness of our security posture.
Acceptable Use Policy
The Samsara knowledge base is a resource for authorized users only. Users are expected to maintain the confidentiality, integrity, and availability of the data within the knowledge base. Unauthorized access, modification, or disclosure of information is strictly prohibited. Users are responsible for protecting their login credentials and reporting any suspected security breaches. This policy is subject to change.
Data Visualization and Reporting

Unlocking the profound insights hidden within your Samsara data requires more than just raw numbers; it demands a clear, insightful visualization that illuminates the path to enhanced operational efficiency and spiritual growth in your organization. This section guides you on transforming your data into compelling narratives that reveal the truth of your operations, fostering a deeper understanding of your journey towards mindful management.
Data Visualization Methods
Effective data visualization is paramount to gleaning actionable intelligence from the Samsara knowledge base. Different visualization methods cater to different data types, revealing unique perspectives on your operational reality. By choosing the right method, you can unveil patterns and trends that might otherwise remain hidden, leading to more informed decision-making.
- Line Charts: Ideal for visualizing time-series data, revealing trends and patterns over time. For example, a line chart could display vehicle mileage over a month, using “Timestamp” as the x-axis and “Mileage” as the y-axis. The chart title would be “Vehicle Mileage Trend,” and a clear legend would differentiate between multiple vehicles if needed. This method provides a clear, intuitive understanding of changes over time, highlighting periods of high or low activity.
This allows for the identification of potential maintenance needs or periods of peak operational efficiency, leading to proactive adjustments in resource allocation and scheduling.
- Bar Charts: Best suited for categorical data, comparing different groups or categories. For instance, a bar chart could compare the average fuel consumption across different vehicle types, using “Vehicle Type” as the x-axis and “Average Fuel Consumption (L/100km)” as the y-axis. The chart would be titled “Fuel Consumption by Vehicle Type,” with a clear legend distinguishing between the types of vehicles.
This method offers a straightforward comparison of distinct categories, making it easy to identify areas for improvement in fuel efficiency or pinpoint vehicles requiring attention.
- Geographical Maps: Excellent for visualizing geographically distributed data, such as the location of assets or the routes taken by vehicles. A map could display the locations of all your vehicles in real-time, using markers to indicate vehicle position and color-coding to represent different vehicle statuses (e.g., idle, moving, in-service). The map title would be “Real-time Vehicle Locations,” and a legend would explain the color-coding scheme.
This method provides a holistic view of your geographically dispersed operations, facilitating efficient fleet management and identifying potential logistical bottlenecks.
Line charts excel at showcasing trends, bar charts facilitate easy comparisons, and geographical maps offer a spatial understanding of data. The choice of method should always align with the type of data and the insights you aim to uncover. Each visualization technique offers a unique lens through which to view your operational reality, leading to a more comprehensive understanding.
Report Generation from Samsara Knowledge Base
Generating reports from the Samsara knowledge base is a straightforward process that empowers you to translate data into actionable knowledge. The following steps Artikel how to create insightful reports using different visualization techniques.
- Data Selection: Identify the specific data fields required for your report. For example, to generate a report on vehicle mileage, you would select the “Timestamp” and “Mileage” fields.
- Filtering and Aggregation: Refine your data by applying filters (e.g., date range, vehicle type). Aggregate data as needed (e.g., calculate average mileage per day). This allows for the focusing of insights on relevant subsets of your overall data.
- Visualization Selection: Choose the appropriate visualization technique (e.g., line chart for mileage over time, bar chart for comparing mileage across vehicle types). The selected technique should reflect the insights you are seeking from the data.
- Report Generation: Use the Samsara reporting tools to generate the report, incorporating your chosen visualization. This typically involves selecting the data, filters, aggregation methods, and the desired visualization type within the platform’s interface.
- Report Export: Export the report in your preferred format (e.g., PDF for formal documentation, CSV for data analysis in other tools). This allows for sharing and utilizing the report’s data across various platforms and applications.
- Customization: Customize the report’s appearance (e.g., add a company logo, adjust fonts) to reflect your brand identity and enhance readability. This step is crucial for creating a professional and impactful report that clearly communicates the insights derived from the data.
By following these steps, you can generate comprehensive reports that effectively communicate key insights from your Samsara data, enabling informed decision-making and operational improvements.
KPI Report
Five key performance indicators (KPIs) can provide a holistic overview of your operational efficiency. These KPIs, visualized appropriately, offer a clear path to identifying areas for improvement and fostering a more mindful approach to fleet management.
| KPI Name | Definition | Calculation Method | Data Source | Current Value (Example) |
|---|---|---|---|---|
| Average Vehicle Mileage | Average distance traveled per vehicle per day | Total Mileage / Total Number of Vehicles / Number of Days | Samsara Vehicle Data | 150 miles |
| Fuel Efficiency | Average fuel consumption per mile driven | Total Fuel Consumed / Total Mileage | Samsara Vehicle Data & Fuel Sensors | 10 mpg |
| Vehicle Uptime | Percentage of time vehicles are operational | (Total Operational Time / Total Time) – 100 | Samsara Vehicle Status Data | 95% |
| Driver Score (Safety) | Average driver performance based on safety metrics | Average of individual driver scores based on harsh braking, acceleration, and cornering | Samsara Driver Behavior Data | 85/100 |
| Maintenance Cost per Vehicle | Average cost incurred for vehicle maintenance per vehicle | Total Maintenance Cost / Total Number of Vehicles | Samsara Maintenance Records | $500/month |
Appropriate visualization for each KPI would include: line charts for tracking trends over time (mileage, fuel efficiency, uptime), bar charts for comparing across vehicle types (maintenance costs), and perhaps a dashboard showing all five KPIs at a glance.
Overall performance indicates a generally healthy operational state. However, a slight dip in fuel efficiency warrants further investigation. Proactive maintenance and driver training programs could enhance these key areas, leading to cost savings and improved safety.
API Interaction with Samsara
Embark on a journey to unlock the profound power of data within the Samsara ecosystem. This section serves as your guide to seamlessly integrating your applications with the Samsara API, allowing you to harness the wealth of information at your fingertips. Consider this your key to unlocking deeper insights and automating processes, all through the elegance of API interaction.
API Authentication and Authorization
The Samsara API employs robust authentication methods to safeguard your data. Understanding these methods is the cornerstone of secure and efficient API integration. Two primary methods are available: API Key and OAuth 2.0. The choice depends on your application’s security needs and architecture.
- API Key Authentication: This method uses a single, long-lived API key. It’s straightforward but requires careful management to prevent unauthorized access. Example using
curl: curl -H "Authorization: Bearer YOUR_API_KEY" "https://api.samsara.com/v1/vehicles/12345"- OAuth 2.0 Authentication: A more secure approach, OAuth 2.0 allows for granular permission control and better security practices. This method involves obtaining an access token using client credentials or the authorization code grant. Example using Python’s
requestslibrary: import requests
response = requests.post('https://api.samsara.com/oauth/token', data='grant_type': 'client_credentials', 'client_id': 'YOUR_CLIENT_ID', 'client_secret': 'YOUR_CLIENT_SECRET')
access_token = response.json()['access_token']
headers = 'Authorization': f'Bearer access_token'
response = requests.get('https://api.samsara.com/v1/vehicles/12345', headers=headers)
API scopes define the level of access your application has. Requesting only necessary scopes enhances security.
| Scope | Description | Example Permissions |
|---|---|---|
read:vehicles | Access to vehicle data | Retrieve vehicle location, diagnostics |
write:sensors | Modify sensor settings | Update sensor thresholds |
read:drivers | Access to driver information | Retrieve driver logs |
manage:alarms | Manage and acknowledge alarms | Acknowledge a specific alarm |
Data Retrieval
Accessing data from Samsara is straightforward. The API provides endpoints for various data types. Efficient retrieval of large datasets requires understanding pagination.
- Retrieving Vehicle Location: Use the
/fleet/vehicles/vehicle_id/locationsendpoint. Example usingcurl: curl -H "Authorization: Bearer YOUR_API_KEY" "https://api.samsara.com/v1/fleet/vehicles/12345/locations"- Pagination: For large datasets, use the
limitandoffsetparameters. Example using Python’srequestslibrary: import requests
limit = 100
offset = 0
while True:
params = 'limit': limit, 'offset': offset
response = requests.get('https://api.samsara.com/v1/fleet/vehicles/12345/locations', headers=headers, params=params)
data = response.json()
# Process data
if len(data['locations']) < limit:
break
offset += limit
Rate limits prevent API abuse. Implement exponential backoff to handle rate limit errors gracefully.
Data Manipulation
Modifying data within the Samsara API allows for dynamic updates and management of your fleet. Proceed with caution, understanding the potential impact of changes.
- Creating a New Sensor: Use the
/sensorsendpoint with aPOSTrequest. Example usingcurl: curl -X POST -H "Authorization: Bearer YOUR_API_KEY" -H "Content-Type: application/json" -d '"name": "New Sensor"' "https://api.samsara.com/v1/sensors"- Updating Vehicle Information: Use the
/fleet/vehicles/vehicle_idendpoint with aPUTrequest. Example using Python’srequestslibrary: import requests
data = 'name': 'Updated Vehicle Name'
response = requests.put(f'https://api.samsara.com/v1/fleet/vehicles/12345', headers=headers, json=data)
Error Handling and Troubleshooting
The Samsara API returns standardized error responses. Effective error handling is crucial for robust applications.
- Common Error Codes: 400 (Bad Request), 401 (Unauthorized), 403 (Forbidden), 404 (Not Found), 500 (Internal Server Error).
- Error Handling Example (Python):
try:
response = requests.get('...', headers=headers)
response.raise_for_status()
# Process successful response
except requests.exceptions.HTTPError as e:
print(f"HTTP Error: e")
except requests.exceptions.RequestException as e:
print(f"Request Error: e")
Specific API Endpoint Examples
Let’s explore practical examples using three key endpoints.
/fleet/vehicles: This endpoint provides vehicle information.GETrequests retrieve data, whilePUTrequests update vehicle details./sensors: This endpoint manages sensors.GETretrieves sensor data,POSTcreates new sensors, andDELETEremoves sensors./drivers: This endpoint manages driver information.GETrequests retrieve driver data.
Rate Limiting and Best Practices
Samsara imposes rate limits to ensure API stability. Adhering to best practices prevents exceeding these limits.
- Rate Limits: Consult the official Samsara API documentation for the most up-to-date rate limits.
- Best Practices: Implement caching, batch requests, and exponential backoff strategies to manage rate limits effectively.
Security Considerations
Protecting your API keys and data is paramount. Implement secure practices to prevent unauthorized access and data breaches.
- Secure Key Storage: Never hardcode API keys directly into your code. Use environment variables or secure configuration management tools.
- Data Encryption: Encrypt sensitive data both in transit and at rest.
- Input Validation: Validate all API requests to prevent injection attacks.
Troubleshooting and Error Handling
Embarking on the journey of data integration and analysis with the Samsara knowledge base is akin to navigating a vast and powerful river. While the currents of information can propel you forward to great insights, unforeseen obstacles—errors—can arise. Understanding how to identify and overcome these challenges is crucial for a successful and fulfilling voyage. This section provides the navigational tools and wisdom needed to chart a course through any turbulent waters you might encounter.The path to mastering Samsara’s data landscape requires patience, perseverance, and a methodical approach to problem-solving.
Just as a skilled navigator consults charts and compasses, you will learn to interpret error messages and apply effective troubleshooting techniques. Remember, each challenge encountered is an opportunity for growth and a deeper understanding of the system.
Common Errors and Their Causes
A variety of errors can occur when interacting with the Samsara knowledge base. These often stem from issues with API keys, authentication failures, incorrect data formats, or network connectivity problems. Understanding the root cause is the first step towards resolution. For example, an “Unauthorized” error typically indicates a problem with your API key or its permissions, while a “404 Not Found” error suggests an incorrect API endpoint or data identifier.
Similarly, malformed JSON data will often result in parsing errors. The key is to carefully examine the error message for clues.
Troubleshooting Steps for Data Access Issues
When encountering problems accessing Samsara data, a structured approach is essential. First, verify your API key is correctly configured and possesses the necessary permissions. Second, double-check the API endpoint URL for accuracy. Third, examine the request parameters and ensure they are formatted correctly and that the required data fields are included. Fourth, investigate any network connectivity issues that might be preventing communication with the Samsara servers.
If the problem persists, consult the Samsara API documentation for detailed specifications and potential solutions. Systematic investigation, like this, allows for swift identification and resolution of the problem.
Troubleshooting Flowchart for API Authentication Failure
This flowchart illustrates the troubleshooting process for an API authentication failure:[Descriptive Flowchart]Imagine a flowchart with distinct boxes and arrows. The first box would be “API Authentication Failure?”. If yes, the arrow points to “Verify API Key Validity.” This box then branches into two possibilities: “Valid Key” (arrow pointing to “Check API Key Permissions”) and “Invalid Key” (arrow pointing to “Regenerate API Key”).
“Check API Key Permissions” branches to “Correct Permissions” (arrow pointing to “Success!”) and “Incorrect Permissions” (arrow pointing to “Update API Key Permissions”). “Regenerate API Key” points directly to “Retry API Call”. The “Success!” box concludes the process. If at any point an action fails, there’s a fallback to “Consult Samsara Documentation.” This provides a visual representation of a structured approach to resolving authentication issues.
Data Backup and Recovery
The preservation of our Samsara knowledge base is a sacred act, a testament to our commitment to wisdom and its enduring legacy. Just as a diligent gardener nurtures their plants, we must diligently protect the fruits of our collective knowledge. Data backup and recovery are not mere technicalities; they are essential practices that safeguard our spiritual growth and the continuity of our shared learning.
Data Backup Methods
The Samsara knowledge base employs a multi-layered approach to data backup, mirroring the multifaceted nature of enlightenment itself. This holistic strategy ensures the resilience and longevity of our invaluable data. We utilize a combination of full, incremental, and differential backups, augmented by continuous data protection (CDP).
Full backups, representing the complete and pristine state of our knowledge, are performed weekly. These backups are stored in geographically diverse cloud storage locations (Amazon S3 and Google Cloud Storage), ensuring redundancy and resilience against unforeseen circumstances. Incremental backups, capturing only the changes since the last full or incremental backup, are performed daily. These are stored in the same geographically distributed cloud locations.
Differential backups, capturing changes since the last full backup, are conducted twice a week and also stored in the same locations. Continuous Data Protection (CDP) provides near real-time data protection, ensuring minimal data loss in case of unforeseen events. CDP data is also stored in the same geographically diverse cloud storage locations.
Our backup infrastructure leverages industry-leading software and hardware. The primary backup software is Veeam Backup & Replication v12, running on Dell PowerEdge servers with 256GB RAM and 16TB of storage. Data is encrypted both in transit and at rest using AES-256 encryption. Access to backups is controlled through role-based access control (RBAC) within the Veeam console, ensuring only authorized personnel can access and manage backups.
| Backup Method | Frequency | Storage Location | Retention Policy | Software/Hardware |
|---|---|---|---|---|
| Full Backup | Weekly | Amazon S3, Google Cloud Storage | 3 months | Veeam Backup & Replication v12, Dell PowerEdge Servers |
| Incremental Backup | Daily | Amazon S3, Google Cloud Storage | 1 week | Veeam Backup & Replication v12, Dell PowerEdge Servers |
| Differential Backup | Twice Weekly | Amazon S3, Google Cloud Storage | 2 weeks | Veeam Backup & Replication v12, Dell PowerEdge Servers |
| CDP | Continuous | Amazon S3, Google Cloud Storage | 24 hours | Veeam Backup & Replication v12, Dell PowerEdge Servers |
Data Recovery Procedures
The path to restoring our data, should the need arise, is a well-defined process, a carefully choreographed dance of precision and grace. Our goal is to minimize downtime and ensure a seamless return to our spiritual pursuits.
Recovery procedures vary depending on the extent of data loss. For single file recovery, the process involves locating the relevant backup, mounting it, and extracting the file. Full database recovery involves restoring the latest full backup and applying subsequent incremental or differential backups. The estimated RTO for single file recovery is under 30 minutes, while full database recovery has an RTO of under 4 hours.
The RPO for full backups is 7 days, for incremental backups is 1 day, for differential backups is 2 days and for CDP is near real-time.
Regular testing of our backup and recovery process is crucial, a form of spiritual discipline ensuring our preparedness. These tests, conducted monthly, involve restoring a sample of data from different backup types to verify data integrity and process efficiency. Potential errors or failures during data recovery are addressed through detailed troubleshooting guides and a dedicated support team.
Backup Strategy Comparison
The selection of a backup strategy is a critical decision, a path we choose to navigate the potential challenges of data loss. We compare three prominent strategies to ensure we select the one most aligned with our values and needs.
We analyze the 3-2-1 backup strategy (three copies of data, on two different media types, with one copy offsite), the Grandfather-Father-Son (GFS) strategy, and a strategy employing only cloud-based backups. Each approach presents a unique balance of cost, complexity, security, and recovery time objectives. The chosen strategy, a hybrid approach combining on-premise and cloud-based backups, prioritizes security, data availability, and cost-effectiveness.
It provides a robust and flexible solution.
| Backup Strategy | Cost | Complexity | RTO | RPO | Security | Advantages | Disadvantages | Suitability for Samsara |
|---|---|---|---|---|---|---|---|---|
| 3-2-1 Backup | Medium | Medium | Low-Medium | Low-Medium | High | Robust redundancy, multiple recovery options | Requires careful planning and management | Highly Suitable |
| Grandfather-Father-Son | Medium | Medium | Medium | Medium | Medium | Efficient storage utilization | More complex recovery process | Suitable |
| Cloud-Only Backup | Low-Medium | Low | Low-Medium | Low-Medium | High | Cost-effective, scalable, geographically dispersed | Reliance on third-party provider | Partially Suitable |
Disaster Recovery Plan
Our disaster recovery plan is a beacon of hope, guiding us through the storms of unforeseen circumstances. It ensures the continuity of our knowledge base, a testament to our resilience.
The plan encompasses failover procedures to a geographically separate cloud-based environment, leveraging Amazon Web Services (AWS) as our secondary data center. Communication protocols include email alerts, SMS notifications, and a dedicated Slack channel. Roles and responsibilities are clearly defined, with designated teams responsible for data recovery, system restoration, and communication. The plan includes regular drills and updates to ensure its effectiveness.
Scalability and Performance: Samsara Knowledge Base

The Samsara knowledge base, like a blossoming lotus, is designed to gracefully expand its capacity to accommodate the ever-growing stream of data. Its strength lies not only in its present capabilities but also in its inherent ability to adapt and thrive under increasing pressure. This section delves into the architecture and strategies employed to ensure both present and future performance.The Samsara knowledge base is built upon a robust, scalable architecture that employs a multi-tiered approach, separating concerns and optimizing resource allocation.
This ensures that even with substantial data growth, the system maintains responsiveness and efficiency. Imagine a mighty river, constantly fed by tributaries, yet maintaining a steady, powerful flow. This is the essence of the Samsara knowledge base’s scalability.
Data Storage and Retrieval Strategies
Efficient data storage and retrieval are the cornerstones of a high-performing knowledge base. The system utilizes a distributed database architecture, allowing data to be spread across multiple servers. This distribution minimizes latency, ensuring rapid access to information regardless of the data volume. Furthermore, advanced indexing techniques and query optimization algorithms are employed to pinpoint the relevant information swiftly.
Consider this akin to a well-organized library, where each book is meticulously cataloged and readily accessible.
Performance Optimization Techniques
Several performance optimization techniques are integrated to ensure the Samsara knowledge base remains swift and responsive. Caching mechanisms store frequently accessed data in memory, reducing the need to repeatedly query the database. Load balancing distributes incoming requests across multiple servers, preventing any single server from becoming overloaded. Regular performance monitoring and analysis identify bottlenecks and allow for proactive adjustments.
Think of a finely tuned engine, each component working in harmony to deliver optimal performance.
Scaling Strategy for Future Growth
To accommodate future growth, a phased scaling strategy is implemented. This strategy includes both vertical scaling (increasing the resources of existing servers) and horizontal scaling (adding more servers to the system). Automated scaling mechanisms dynamically adjust resources based on real-time demand, ensuring optimal performance under varying loads. Regular capacity planning exercises predict future needs and guide proactive infrastructure upgrades.
This proactive approach ensures that the Samsara knowledge base can gracefully adapt to any growth spurt, like a sturdy tree with strong roots, ready to weather any storm. For example, a company experiencing a 50% increase in user base in the past year would trigger an increase in server capacity, allowing the system to maintain its responsiveness without any performance degradation.
Samsara Knowledge Base Best Practices
The path to enlightenment in data management lies in cultivating a robust and reliable knowledge base. Just as a skilled gardener nurtures their plants, we must tend to our data, ensuring its integrity, performance, and security. This section reveals the secrets to achieving this harmonious balance within the Samsara knowledge base. Through mindful practices, we can unlock the full potential of our data, transforming it from a mere collection of facts into a source of wisdom and insight.Maintaining data integrity is paramount.
It is the foundation upon which all other aspects of the knowledge base rest. Without it, our insights become clouded, our decisions fallible, and our progress hindered. Therefore, we must diligently cultivate practices that ensure the accuracy, consistency, and completeness of our data.
Data Integrity Maintenance
Regular data audits are essential for identifying and correcting inconsistencies. These audits should be conducted at predetermined intervals, using established checklists and procedures to ensure thoroughness. Data validation rules should be implemented to prevent the entry of incorrect or incomplete information. For instance, a rule could be implemented to ensure that all date fields are populated with valid dates in the correct format.
Furthermore, version control should be employed to track changes and revert to previous versions if necessary. This ensures that we can always trace the history of our data and identify the source of any errors. Employing a robust system of checks and balances, akin to the intricate workings of the universe itself, is crucial for maintaining data integrity.
Knowledge Base Performance Optimization
The swift retrieval of information is crucial. A slow-performing knowledge base hinders productivity and frustrates users. To ensure optimal performance, regular database maintenance is necessary. This includes tasks such as indexing, optimizing queries, and removing outdated or unnecessary data. Regular review of database queries to identify and optimize slow-performing queries is also crucial.
This could involve using database profiling tools to pinpoint bottlenecks. Consider the analogy of a well-oiled machine; regular maintenance keeps it running smoothly and efficiently. By optimizing the database structure and ensuring efficient query execution, we can achieve a state of effortless data access.
Data Security and Compliance Strategies
Protecting our data is a sacred duty. Data breaches can have devastating consequences, leading to financial losses, reputational damage, and legal repercussions. To mitigate these risks, we must implement robust security measures, including access control, encryption, and regular security audits. Access control mechanisms should restrict access to sensitive data based on roles and responsibilities. Data encryption protects data both at rest and in transit.
Regular security audits help identify and address vulnerabilities before they can be exploited. Furthermore, we must ensure that our practices comply with all relevant regulations and standards, such as GDPR and CCPA. This mindful approach to data security ensures the sanctity and protection of our valuable information. Consider data security as a protective shield, safeguarding our knowledge and wisdom from external threats.
Data Modeling and Schema Design
The design of the Samsara knowledge base’s data model is a crucial step in its journey towards enlightenment – a path towards efficient data storage, retrieval, and analysis. A well-structured schema is the foundation upon which we build a robust and scalable system, ensuring the seamless flow of information and the illumination of insights. Just as a skilled architect carefully crafts the blueprint for a temple, we meticulously design our data model to support the knowledge base’s purpose and future growth.The data model employed in the Samsara knowledge base utilizes a relational approach, mirroring the interconnectedness of all things.
This model organizes data into tables, each representing a specific entity (like articles, users, or categories), with relationships defined between these tables to reflect the natural connections within the knowledge base. This structured approach allows for efficient querying and data integrity, ensuring clarity and preventing inconsistencies, much like the precise alignment of stars in a celestial map.
Relational Data Model Description
The core of our relational model revolves around a central table, the “Articles” table, which stores the main content of the knowledge base. This table contains fields such as article ID, title, content, author, creation date, and category IDs. Other tables, such as “Categories” and “Users,” are linked to the “Articles” table through foreign keys, enabling efficient retrieval of articles based on category or author.
This interconnectedness, like the intricate web of life, allows us to easily navigate and explore the wealth of knowledge within the Samsara knowledge base. Relationships are carefully designed to ensure data integrity and efficiency, preventing redundancy and ensuring that information is consistent across the system.
Schema Design and Modification Process
The process of designing and modifying the schema follows a disciplined and iterative approach, guided by the principles of simplicity and clarity. Initial design involves careful consideration of the data requirements, identifying entities and their attributes. This phase involves close collaboration with stakeholders to ensure that the model accurately reflects the needs of the knowledge base. Subsequent modifications are carefully planned and implemented, following a structured change management process.
Each change is thoroughly tested to ensure that it does not compromise the integrity or performance of the system. This methodical approach ensures the ongoing stability and reliability of the knowledge base, akin to the careful tending of a sacred garden.
Comparison of Data Modeling Approaches
While the relational model forms the core of our knowledge base, it’s important to acknowledge other approaches. NoSQL databases, for example, offer scalability and flexibility for handling unstructured or semi-structured data. However, for the Samsara knowledge base, with its focus on structured information and the need for complex queries, the relational model provides a superior foundation. The structured nature of relational databases ensures data integrity and allows for efficient querying, supporting the knowledge base’s need for accurate and readily accessible information.
Choosing the right model is like selecting the perfect tool for a specific task – the relational model is the ideal instrument for our purpose, offering the precision and control necessary to manage the knowledge base effectively.
Real-world Applications of Samsara Data
The Samsara knowledge base, a reservoir of meticulously gathered insights, transcends mere data storage; it’s a wellspring of transformative potential, empowering businesses to navigate the complexities of their operations with unparalleled clarity and efficiency. Unlocking this potential requires understanding how its data translates into tangible, real-world improvements across diverse industries. The journey towards enlightenment, in this context, is paved with data-driven decisions that lead to enhanced productivity, optimized resource allocation, and ultimately, a more harmonious and prosperous enterprise.The power of Samsara data lies in its ability to illuminate the hidden patterns within operational processes.
By providing a holistic view of various aspects – from vehicle performance and driver behavior to equipment utilization and environmental conditions – it empowers businesses to make informed decisions, optimize resource allocation, and proactively address potential issues before they escalate into significant problems. This proactive approach not only saves resources but also fosters a culture of continuous improvement, leading to enhanced operational efficiency and increased profitability.
Transportation and Logistics
Samsara data offers a powerful toolkit for transportation and logistics companies. Real-time tracking of vehicles allows for optimized routing, reducing fuel consumption and delivery times. Analyzing driver behavior patterns helps identify areas for improvement in safety and efficiency, leading to lower insurance premiums and improved driver performance. For example, a large trucking company used Samsara data to identify a pattern of excessive idling in certain areas, leading to a targeted training program that reduced fuel consumption by 15% within six months.
This not only saved the company significant money but also contributed to a reduction in its carbon footprint.
Construction and Field Services
In the construction and field services industries, Samsara data provides critical insights into equipment utilization and maintenance. By monitoring equipment operating hours, location, and performance metrics, companies can schedule preventative maintenance effectively, minimizing downtime and extending the lifespan of their assets. Real-time location tracking also enhances project management, enabling supervisors to monitor the progress of work crews and ensure timely completion of projects.
Consider a scenario where a construction company uses Samsara to monitor the location and operational status of its heavy equipment. Identifying a piece of equipment operating outside its normal parameters triggers an alert, prompting immediate maintenance and preventing a potential breakdown that could delay the project by days or even weeks, ultimately saving significant costs.
Manufacturing and Warehousing
Samsara data plays a vital role in optimizing operations within manufacturing and warehousing facilities. By tracking the movement of goods and equipment, companies can streamline workflows, improve inventory management, and reduce waste. Real-time visibility into the location of assets enables faster retrieval and reduces search time, leading to improved productivity and efficiency. Imagine a manufacturing plant utilizing Samsara to track the movement of materials throughout the production process.
By identifying bottlenecks in the workflow, managers can implement process improvements, leading to increased output and reduced production costs. The data also provides insights into equipment utilization, allowing for better scheduling and resource allocation.
My dear students, the Samsara knowledge base offers a vast ocean of wisdom, guiding you through life’s complexities. To truly navigate this ocean, consider supplementing your studies with the practical insights found in the evolt 360 knowledge base , a valuable resource that complements our teachings. Returning to Samsara’s wisdom, remember that true understanding blooms from a blend of theoretical knowledge and practical application.
Future Trends and Developments
The Samsara knowledge base, a beacon of wisdom guiding us through the complexities of data, is not static. Like the ever-flowing river of Samsara itself, it is in constant evolution, adapting to the ever-changing technological landscape and the needs of its users. This section explores the exciting future trends and advancements that will shape the Samsara knowledge base, transforming it into an even more powerful and insightful tool.
We will examine how emerging technologies, such as AI and blockchain, will enhance its functionality, accessibility, and security, ultimately enriching the user experience and empowering a deeper understanding of the data within.
Future Trends in Samsara Knowledge Base Functionality
The future of the Samsara knowledge base hinges on enhancing user interaction and access to information. This will be achieved through advancements in UI/UX design and the integration of sophisticated AI-powered tools.
- Improved Search Functionality and Personalization: The user interface will evolve to incorporate conversational interfaces, allowing users to interact with the knowledge base in a more natural and intuitive way. AI-powered search assistants will anticipate user needs, proactively suggesting relevant articles and reducing search time. Imagine a scenario where a user simply types “troubleshooting sensor error” and the system immediately presents the most relevant solution, complete with videos and interactive diagrams.
This will improve user experience significantly, leading to increased user satisfaction and reduced reliance on support staff.
- Advancements in Natural Language Processing (NLP): NLP will revolutionize search capabilities, enabling semantic search—understanding the meaning behind search queries, not just s. This will dramatically improve search accuracy. For example, a query like “Why is my sensor data inaccurate?” will not only return articles about sensor inaccuracies but also those discussing potential causes like faulty calibration or network issues. We project a reduction in search time by 25% and an increase in the accuracy of search results by 40% through the implementation of advanced NLP algorithms.
- Blockchain Integration for Enhanced Data Security: Blockchain technology can be integrated to ensure the immutability and transparency of knowledge base data. Each update or modification can be recorded on a secure, tamper-proof ledger, providing a verifiable audit trail and bolstering data integrity. This is especially crucial for regulated industries where data provenance is paramount. For example, the use of blockchain can ensure that any changes to critical documentation are properly tracked and verified, mitigating risks associated with data tampering or unauthorized alterations.
Impact of Emerging Technologies on Samsara Knowledge Base Capabilities
The integration of emerging technologies will not only improve the user experience but also significantly enhance the capabilities of the Samsara knowledge base.
- Machine Learning (ML) for Enhanced Relevance: ML algorithms can analyze user behavior and content usage patterns to provide highly personalized content recommendations and automated knowledge base updates. Anomaly detection in data will flag inconsistencies or potential errors, prompting timely interventions. Predictive maintenance of the knowledge base infrastructure can anticipate and prevent outages, ensuring continuous availability. For instance, ML can predict when a particular article needs updating based on user feedback and the frequency of related support tickets.
- Augmented and Virtual Reality (AR/VR) for Enhanced Training: AR/VR technologies can create immersive training experiences, allowing users to interact with the knowledge base in a more engaging and effective way. Interactive tutorials and remote expert assistance through AR overlays can dramatically improve knowledge retention and problem-solving capabilities. Imagine technicians using AR glasses to overlay interactive instructions onto real-world equipment, guiding them through complex repair procedures.
- Managing Increased Data Volume from IoT: The exponential growth of IoT data will require robust scalability solutions. This includes employing advanced data storage and processing techniques, such as cloud-based solutions and distributed databases. Implementing efficient data compression and indexing strategies will be critical for maintaining optimal performance even with massive data volumes. We will proactively adapt our infrastructure to accommodate the anticipated increase in data volume, ensuring the knowledge base remains responsive and efficient.
Areas for Improvement and Innovation in the Samsara Knowledge Base
Continuous improvement is the path to enlightenment in the realm of knowledge management. The following table Artikels key areas for improvement and the strategies to achieve them.
| Area for Improvement | Specific Examples | Potential Solutions | Measurable Outcomes |
|---|---|---|---|
| Knowledge Base Organization & Structure | Inconsistent tagging, outdated information, difficulty finding relevant articles | Implement a robust taxonomy, automated content updates, user feedback mechanisms | Improved search accuracy (measured by increased click-through rate on relevant results), reduced search time (measured by average time to find relevant information), higher user satisfaction (measured by user surveys) |
| Content Quality & Relevance | Inaccurate or incomplete information, lack of multimedia content | Establish content quality guidelines, integrate multimedia assets (videos, images), implement peer review process | Increased user engagement (measured by time spent on articles and number of page views), improved knowledge retention (measured by post-training assessments), reduced support tickets (measured by ticket volume) |
| User Accessibility & Inclusivity | Lack of accessibility features for users with disabilities, limited language support | Implement accessibility features (screen readers, keyboard navigation), translate content into multiple languages | Improved user inclusivity (measured by increased usage from diverse user groups), wider user base (measured by geographic reach and user demographics), increased accessibility compliance (measured by adherence to WCAG guidelines) |
| Integration with other Systems | Limited integration with other business systems, data silos | Develop APIs for seamless integration, establish data exchange protocols | Improved data flow (measured by reduced data latency), enhanced data analysis (measured by increased insights derived from integrated data), reduced data redundancy (measured by decreased data storage costs) |
Long-Term Vision for the Samsara Knowledge Base
The Samsara knowledge base will be a self-evolving, AI-powered ecosystem of knowledge, seamlessly integrating with all business systems, providing intuitive access to relevant information for every user, and continuously improving its accuracy and relevance through machine learning and user feedback. It will be a scalable, secure, and universally accessible resource, empowering informed decision-making and fostering continuous learning across the organization.
Security Audits and Compliance
The path to enlightenment in data management involves not just harnessing the power of knowledge, but also safeguarding its sanctity. Security audits and compliance are the guardians of this sacred trust, ensuring the Samsara knowledge base remains a haven of secure and reliable information. This section illuminates the practices and principles that uphold this integrity.The process of conducting security audits for the Samsara knowledge base is a multifaceted journey, demanding a holistic approach.
It’s not merely a technical exercise; it’s a spiritual practice of vigilance and continuous improvement.
Security Audit Process
A comprehensive security audit involves a systematic review of all aspects of the knowledge base’s security posture. This includes assessing the physical security of servers (if applicable), network security, access controls, data encryption methods, and the vulnerability of the software and systems used. The process typically follows a structured methodology, often involving penetration testing, vulnerability scanning, and code reviews.
Regular audits, perhaps annually or semi-annually, are essential to maintain a strong security profile. A well-documented audit trail, including findings, remediation steps, and timelines, is crucial for accountability and continuous improvement.
Compliance Requirements and Regulations
The Samsara knowledge base must adhere to a range of compliance requirements and regulations, depending on the nature of the data it holds and the industry it serves. These may include regulations such as GDPR (General Data Protection Regulation) for personal data, HIPAA (Health Insurance Portability and Accountability Act) for healthcare data, or PCI DSS (Payment Card Industry Data Security Standard) for payment card information.
Understanding and adhering to these regulations is not just a legal obligation; it’s an ethical commitment to protecting the privacy and security of sensitive information. Compliance requires meticulous attention to detail and continuous monitoring of evolving regulatory landscapes.
Ensuring Data Security and Compliance Best Practices
Achieving and maintaining data security and compliance is an ongoing process, not a destination. It demands a culture of security awareness, where every individual involved in the management of the Samsara knowledge base understands their role in protecting sensitive information. This includes implementing robust access control mechanisms, utilizing strong encryption techniques for data both in transit and at rest, and regularly updating software and systems to patch known vulnerabilities.
Employee training on security best practices, including phishing awareness and password management, is vital. Regular security assessments, penetration testing, and vulnerability scanning are essential components of a proactive security posture. Finally, a well-defined incident response plan is crucial for handling security breaches effectively and minimizing potential damage. This plan should include procedures for containment, eradication, recovery, and post-incident analysis.
By embracing these practices, the Samsara knowledge base can strive towards a state of unwavering security and compliance, reflecting a commitment to both technical excellence and ethical responsibility.
FAQ Explained
What types of visualizations are best suited for different data types within Samsara?
Time series data is ideally visualized with line charts or area charts to show trends over time. Categorical data is well-represented by bar charts or pie charts to compare different categories. Geographical data benefits from map visualizations to show location-based information.
How does Samsara handle data breaches?
Samsara employs multiple layers of security, including encryption, access controls, and intrusion detection systems. In the event of a breach, a detailed incident response plan is activated, involving immediate containment, investigation, and remediation efforts, alongside notification of affected parties as required by regulations.
What are the limitations of the Samsara API?
While the Samsara API is powerful, it has rate limits to prevent abuse. Understanding and adhering to these limits is crucial for maintaining consistent access. Additionally, specific data access may be restricted based on user roles and permissions.
Can I customize the Samsara Knowledge Base interface?
The level of customization depends on the specific implementation and access level. While the core functionality is generally standardized, certain aspects like dashboards and report templates might offer customization options.
How often should I back up my Samsara data?
The frequency of backups depends on your data sensitivity and recovery requirements. A combination of full and incremental backups, scheduled regularly (daily or more frequently for critical data), is a common best practice.


