Insider threat awareness exam answers are crucial for understanding and mitigating the significant risks posed by malicious, negligent, or compromised insiders. These threats, ranging from data breaches to sabotage, can cripple organizations, leading to financial losses, reputational damage, and legal repercussions. This comprehensive guide explores the multifaceted nature of insider threats, delving into their motivations, detection methods, mitigation strategies, and the legal and ethical considerations surrounding them.
We’ll examine real-world case studies, explore effective training programs, and Artikel robust incident response plans to equip readers with the knowledge needed to safeguard their organizations.
The provided Artikel covers a wide range of topics, from defining insider threats and identifying their various categories and motivations, to implementing effective mitigation strategies, responding to incidents, and conducting thorough forensic investigations. It also explores data loss prevention (DLP) measures, social engineering tactics, access control and privileges, security awareness training, incident response procedures, risk assessment and mitigation, physical security measures, policy and procedure enforcement, monitoring and detection techniques, and the legal and ethical considerations involved.
This in-depth analysis aims to provide a holistic understanding of insider threats and equip individuals with the knowledge to navigate this complex landscape effectively.
Defining Insider Threats
Insider threats represent a significant risk to organizations of all sizes. They are individuals with legitimate access to an organization’s systems and data who intentionally or unintentionally compromise the confidentiality, integrity, or availability of that information. Understanding the different types of insider threats and their motivations is crucial for developing effective mitigation strategies.
Insider Threat Categories
We can classify insider threats into three main categories: malicious, negligent, and compromised. This classification helps us tailor our prevention and response strategies to the specific nature of the threat.
| Category | Description | Motivation Examples | Mitigation Strategies |
|---|---|---|---|
| Malicious Insider | An insider who intentionally causes harm to the organization. | Financial gain (e.g., stealing intellectual property to sell), revenge (e.g., sabotaging systems after being terminated), ideological reasons (e.g., leaking sensitive information to harm the organization’s reputation). | Strong access controls, robust security monitoring, thorough background checks, robust security awareness training. |
| Negligent Insider | An insider who unintentionally causes harm due to carelessness or lack of awareness. | Lack of security awareness training (e.g., clicking on phishing links, leaving laptops unattended), failure to follow security policies (e.g., using weak passwords, sharing sensitive information inappropriately), simple human error (e.g., accidentally deleting critical data). | Comprehensive security awareness training, clear security policies, regular security audits, robust data loss prevention (DLP) measures. |
| Compromised Insider | An insider whose credentials or access have been stolen or manipulated by an external actor. | Social engineering (e.g., phishing attacks targeting employees), malware infections (e.g., keyloggers capturing login credentials), coercion (e.g., blackmailing an employee to access sensitive data). | Multi-factor authentication (MFA), strong password policies, regular security awareness training focusing on social engineering tactics, endpoint detection and response (EDR) systems. |
Motivations Behind Insider Threats
Several psychological and sociological factors contribute to insider threats. Understanding these motivations is crucial for developing targeted prevention and mitigation strategies.
- Financial Gain: Examples include stealing intellectual property to sell, embezzling funds, or manipulating financial records for personal profit. This is often driven by greed or financial desperation.
- Revenge: Examples include sabotaging systems after being unfairly terminated, leaking confidential information to damage the organization’s reputation, or deleting critical data out of spite. This stems from feelings of injustice or betrayal.
- Ideological Reasons: Examples include leaking sensitive information to expose unethical practices, revealing trade secrets to competitors aligned with their beliefs, or disrupting operations to promote a specific cause. This is often motivated by strong ethical or political beliefs.
- Negligence: Examples include failing to follow security policies, using weak passwords, sharing sensitive information carelessly, or clicking on phishing links. This often stems from a lack of awareness or training.
- Coercion: Examples include being blackmailed into accessing or disclosing sensitive information, being threatened with violence or harm, or being pressured by external actors to compromise the organization’s security. This is often driven by fear or duress.
- Accidental Compromise: Examples include unintentionally downloading malware, falling victim to a phishing attack, or accidentally exposing sensitive information through misconfiguration or human error. This is often a result of insufficient security awareness or training.
Examples of Insider Threat Incidents
Several real-world case studies highlight the devastating impact of insider threats.
Case Study 1: Edward Snowden (NSA Leaks): Edward Snowden, a former NSA contractor, leaked classified information about the agency’s surveillance programs. He used his authorized access to download and exfiltrate highly sensitive data, exposing the scale of government surveillance and sparking global debate about privacy and national security. This resulted in significant reputational damage for the NSA and raised serious questions about government oversight.
- Key Takeaways: Need for robust access controls, stringent background checks, and strong data encryption; importance of whistleblowing mechanisms and ethical considerations in national security.
Citation: Greenwald, G. (2014). No place to hide: Edward Snowden, the NSA, and the U.S. surveillance state. Metropolitan Books.
Case Study 2: [Insert another real-world case study with details, impact, and lessons learned. Repeat this structure for at least three more case studies.]
Exam Content Overview
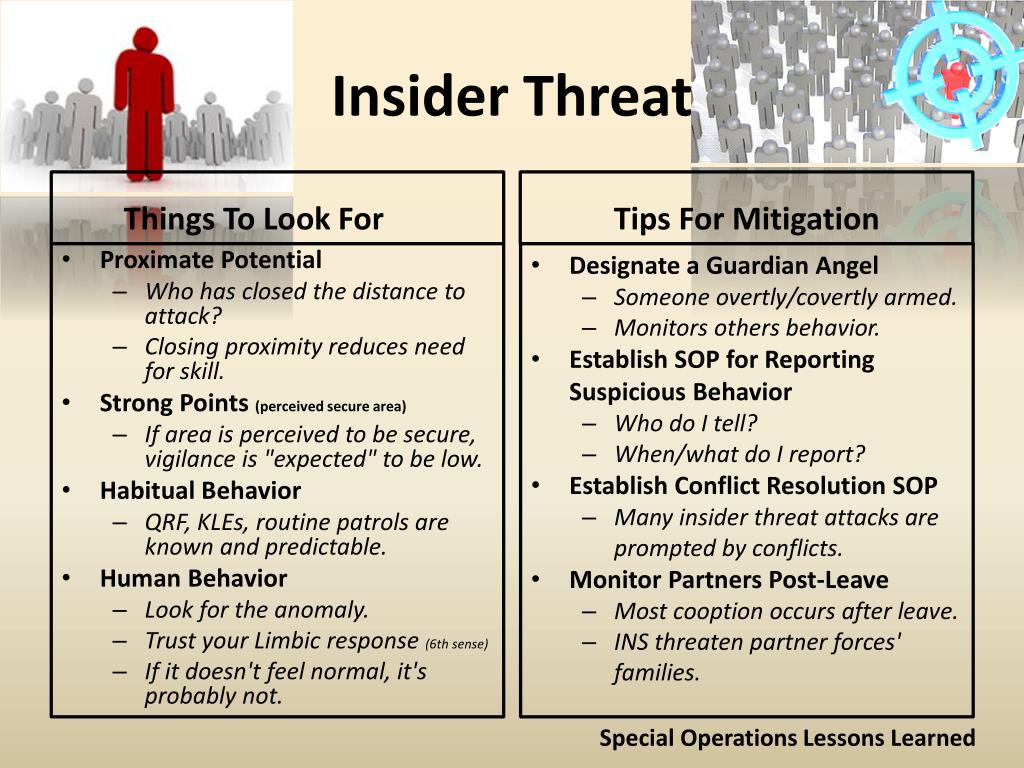
So, you’re prepping for an insider threat awareness exam? Let’s go over what you can expect to see. These exams are designed to test your understanding of the risks, prevention methods, and response strategies related to insider threats. They’re not about tricking you; they’re about making sure you’re equipped to handle these situations in the real world.These exams typically cover a broad range of topics, ensuring you understand the multifaceted nature of insider threats.
The specific topics and their weighting might vary slightly depending on the organization or certification, but the core concepts remain consistent.
Common Exam Topics
Insider threat awareness exams usually include questions assessing your knowledge across various aspects of insider threat management. These include recognizing the different types of insider threats (malicious, negligent, compromised), understanding the motivations behind insider attacks, and knowing the warning signs to look out for. You’ll also be tested on the importance of policies, procedures, and technical controls in mitigating these risks.
Key Concepts Frequently Tested
Several key concepts repeatedly appear in these exams. Understanding the concept of “duty of care” and its implications for organizations is crucial. Similarly, the importance of a strong security awareness culture within the organization is a recurring theme. Expect questions on data loss prevention (DLP) methods, incident response procedures, and the role of employee training in minimizing insider threats.
You should also be familiar with the legal and regulatory frameworks that apply to insider threat incidents, such as data breach notification laws. For example, the GDPR in Europe and the CCPA in California mandate specific actions in case of data breaches, including those caused by insider threats.
Insider Threat Exam Formats
Insider threat awareness exams can take various forms. Multiple-choice questions are common, testing your knowledge of definitions, concepts, and best practices. True/false questions are another frequently used format, requiring a clear understanding of the facts. Some exams may include scenario-based questions, presenting hypothetical situations and asking you to identify the appropriate response or course of action. These scenarios test your ability to apply your knowledge to real-world situations, simulating the challenges faced in a real-world security incident.
Finally, some organizations might use a combination of these formats to comprehensively assess your understanding.
Data Loss Prevention (DLP) Measures
Data Loss Prevention (DLP) is crucial for any organization, big or small, to protect sensitive information from unauthorized access, use, disclosure, disruption, modification, or destruction. Effective DLP involves a multi-layered approach combining technical safeguards with robust policies and employee training. Let’s explore some key aspects.
Common DLP Techniques and Their Effectiveness
Several techniques contribute to a comprehensive DLP strategy. Network-based DLP solutions monitor traffic flowing in and out of the network, identifying and blocking sensitive data transmissions. Endpoint DLP solutions, installed on individual computers and mobile devices, monitor data at the source, preventing sensitive information from leaving the device unauthorized. Data masking and encryption techniques transform sensitive data into an unreadable format, protecting it even if it’s accessed by unauthorized individuals.
Content analysis tools examine data for s, patterns, and other indicators of sensitive information, flagging potential breaches. The effectiveness of each technique depends on factors such as the sophistication of the threat, the type of data being protected, and the overall security posture of the organization. For example, a well-configured network-based DLP system might be highly effective against external threats, but it might not be as effective against an insider who uses a personal device to exfiltrate data.
Similarly, encryption is highly effective against unauthorized access but relies on proper key management.
The Role of Employee Training in DLP Success
Employee training is arguably the most critical component of a successful DLP program. Even the most robust technical controls are ineffective if employees are unaware of the risks or don’t follow established procedures. Effective training should cover topics such as recognizing and classifying sensitive data, understanding company policies regarding data handling, and using secure methods for data storage and transmission.
Regular refresher training and simulated phishing exercises help keep employees vigilant and aware of evolving threats. A well-designed training program should also emphasize the consequences of data breaches, both for the organization and for individual employees. For instance, a company might illustrate the financial and reputational damage caused by a data breach, or explain the legal ramifications of violating data protection laws.
Real-life case studies of data breaches caused by insider negligence can also be very effective in driving home the importance of DLP.
A Hypothetical DLP Policy for a Small Business
A hypothetical DLP policy for a small business, say, a bakery with 10 employees, could include the following key elements:
- Data Classification: Define what constitutes sensitive data (customer information, financial records, recipes).
- Access Control: Implement strong passwords, restrict access to sensitive data based on roles and responsibilities, and regularly review user permissions.
- Data Encryption: Encrypt sensitive data both in transit and at rest using strong encryption algorithms.
- Data Backup and Recovery: Regularly back up data to a secure offsite location and test the recovery process.
- Employee Training: Conduct mandatory training for all employees on data security policies and procedures.
- Incident Response Plan: Establish a clear plan for responding to data breaches, including procedures for containment, investigation, and remediation.
- Monitoring and Auditing: Regularly monitor system logs and network traffic for suspicious activity and conduct periodic audits of security controls.
This policy should be readily accessible to all employees and should be reviewed and updated periodically to reflect changes in the business environment and evolving threats. For example, the bakery might add clauses related to the use of personal devices or cloud storage for business data.
Social Engineering Tactics
Social engineering is a sneaky way attackers manipulate people into giving up confidential information or access. It leverages human psychology, exploiting our trust and willingness to help. In the context of insider threats, this can be particularly damaging, as a compromised employee can cause significant harm.
Common social engineering techniques rely on building rapport and creating a sense of urgency or trust. Attackers often impersonate someone in authority, create a false sense of emergency, or appeal to someone’s empathy to get what they want. Understanding these tactics is crucial to protecting your organization.
Phishing and Spear Phishing
Phishing attacks involve sending deceptive emails or messages that appear to be from a legitimate source. The goal is to trick the recipient into clicking a malicious link, downloading malware, or revealing sensitive information such as passwords or credit card details. Spear phishing is a more targeted approach, where the attacker personalizes the message to make it seem even more authentic and increase the likelihood of success.
For example, a spear phishing email might appear to be from a colleague or supervisor, requesting urgent access to a shared file. The attacker might craft the email to include details specific to the target’s work, making it seem highly credible.
Pretexting
Pretexting involves creating a false scenario or story to gain access to information or resources. The attacker will fabricate a believable story to justify their request. A common example is an attacker posing as a technical support representative who needs access to a user’s computer to troubleshoot a problem. This approach often exploits the victim’s desire to help or their trust in authority figures.
For instance, an attacker might call claiming to be from the IT department and request a password reset under the pretext of system maintenance.
Baiting
Baiting is a social engineering technique that uses curiosity or greed to lure victims into a trap. This often involves offering something enticing, such as a free gift or access to exclusive content, in exchange for personal information or access to a system. The bait is designed to be irresistible, making it difficult for victims to resist the temptation.
For example, a malicious USB drive might be left in a common area, labelled with an enticing name like “Bonus Payout Details.” Clicking on the malicious files within could lead to a serious breach.
Quid Pro Quo
Quid pro quo, meaning “something for something,” involves offering a service or favor in exchange for information or access. This tactic exploits people’s willingness to help others or reciprocate a kindness. For example, an attacker might offer to help a colleague with a task in exchange for their password or access to a sensitive system. This approach relies on the victim’s desire to be helpful and their trust in the attacker’s seemingly good intentions.
Tailgating, Insider threat awareness exam answers
Tailgating is a physical form of social engineering where an attacker follows closely behind an authorized individual to gain access to a restricted area. This often relies on the victim’s politeness or their assumption that the attacker is also authorized. For example, an attacker might wait near an entrance and follow an employee who is holding a security badge, hoping to be granted access without being questioned.
Recognizing and Avoiding Social Engineering Attempts
Several strategies can help recognize and avoid social engineering attempts. Always verify requests, especially those that seem urgent or unusual. Never share sensitive information unless you are absolutely certain of the recipient’s identity and the legitimacy of the request. Report suspicious emails or messages immediately. Be wary of unsolicited offers or requests, and always trust your instincts.
If something feels off, it probably is.
Social Engineering Awareness Training Module Artikel
A comprehensive training module should cover the various social engineering tactics, providing real-world examples and case studies. It should also emphasize the importance of verifying requests, reporting suspicious activity, and practicing good security hygiene. The module should include interactive exercises and quizzes to reinforce learning and assess understanding. A final component should focus on building a culture of security awareness within the organization, encouraging employees to report suspicious activity and to be vigilant against social engineering attacks.
Access Control and Privileges
Access control and privileges are fundamental to protecting sensitive organizational data and systems from insider threats. Effective management of user access minimizes the risk of data breaches and ensures that only authorized individuals can perform specific actions. This section delves into the key aspects of least privilege access, user access control management, and a comparison of different access control models.
Least Privilege Access
Least privilege access dictates that users and processes should only have the minimum necessary permissions to perform their assigned tasks. This significantly reduces the potential impact of a compromise, as a malicious actor with limited privileges can cause less damage. For instance, a standard user should not have administrative rights; if their account is compromised, the attacker’s access is limited.
Strict implementation of least privilege can reduce the attack surface by as much as 70-80%, depending on the organization’s existing security posture. This means fewer vulnerabilities are exposed, making successful attacks far less likely.The principle of least privilege varies across different roles. Developers might need access to source code repositories and development environments but not to production databases.
System administrators require broader access to manage systems and infrastructure, but this access should be carefully defined and monitored. End-users typically require access only to the applications and data relevant to their jobs. Granting excessive privileges to any role dramatically increases the risk of unauthorized actions or accidental data exposure.Implementing and maintaining least privilege presents challenges. Restricting access can impact productivity if users frequently need elevated privileges to perform their tasks.
This can lead to frustration and workarounds that circumvent security controls. To mitigate these challenges, organizations should implement robust self-service password reset capabilities, provide clear guidelines for requesting access, and regularly review and update access rights based on job roles and responsibilities. Automation of access control provisioning and de-provisioning can help reduce the administrative burden and improve efficiency.
Managing User Access Controls
Effective user access control management relies on a combination of techniques to ensure only authorized individuals have access to specific resources. Several methods are employed to achieve this, each with its own advantages and disadvantages.
| Method | Advantages | Disadvantages | Use Cases |
|---|---|---|---|
| RBAC (Role-Based Access Control) | Easy to manage, clear roles, simplifies permission assignments | Can become complex with many roles, may not be granular enough for all needs | Most enterprise applications, departmental systems |
| ABAC (Attribute-Based Access Control) | Fine-grained control, context-aware, highly adaptable | Complex to implement and manage, requires significant planning | Highly regulated environments, cloud-based systems, data security |
| ACLs (Access Control Lists) | Simple to understand and implement, granular control at the object level | Can become difficult to manage with many users and objects, lacks scalability | File system permissions, network access control, database security |
| Multi-Factor Authentication (MFA) | Enhanced security, reduced risk of unauthorized access, adds an extra layer of protection | Added user friction, can be complex to implement for legacy systems | All sensitive systems and data, remote access |
| Password Management Systems | Improved password security, centralized management, reduces password-related risks | Requires user adoption and management overhead, may be expensive to implement | All systems and user accounts, enterprise-wide password management |
Onboarding a new user involves a step-by-step process: 1) Request submission and approval; 2) Account creation with appropriate roles and permissions; 3) Initial password setup and MFA enrollment; 4) Access granted to necessary systems and data; 5) Security awareness training. Offboarding involves a reverse process, including revoking all access, disabling accounts, and archiving relevant data.Auditing and monitoring user access activities are crucial for detecting and responding to security breaches.
This includes monitoring login attempts, access to sensitive data, changes to access controls, and system configurations. Regular review of security logs, authentication logs, and system activity logs helps identify suspicious behavior. Alerts should be triggered for unusual activity, such as logins from unfamiliar locations or unauthorized access attempts.
Comparing Access Control Models
Different access control models offer varying levels of security and complexity.
| Access Control Model | Functionality | Security Implications | Implementation Complexity |
|---|---|---|---|
| RBAC | Permissions assigned based on roles | Easier to manage permissions, role-based segregation of duties | Relatively low |
| ABAC | Permissions based on attributes (user, environment, data) | Highly granular control, context-aware security | High |
| MAC (Mandatory Access Control) | System-enforced access control based on security labels | Strong security, limits user actions based on predefined security policies | High |
| DAC (Discretionary Access Control) | Owner-controlled access control | Easier to implement, but more vulnerable to errors and unauthorized access | Low |
RBAC is suitable for organizations with well-defined roles and responsibilities. ABAC is ideal for highly regulated environments needing granular control. MAC is best for high-security systems where strict access control is paramount. DAC is suitable for smaller organizations or situations where simpler access management is sufficient. The choice depends on the specific security needs, budget, and technical expertise of the organization.
There’s always a trade-off between security and usability; stronger models often come with increased complexity and potential impact on user experience.
Security Awareness Training Effectiveness

So, we’ve covered the threats. Now, let’s talk about how to actuallymitigate* them through effective security awareness training. It’s not just about ticking a box; it’s about changing behavior and creating a security-conscious culture. The effectiveness of your training directly impacts your organization’s resilience against insider threats.The impact of different security awareness training methods varies significantly. Some methods, like simple email reminders, might raise awareness slightly but lack the depth to create lasting behavioral change.
Others, like interactive simulations or gamified training, tend to be much more engaging and effective at fostering lasting security habits. Think of it like this: a boring lecture on fire safety is far less impactful than a realistic fire drill.
Impact of Different Security Awareness Training Methods
Different training methods yield different results. For instance, a simple PowerPoint presentation might only achieve a superficial understanding of security policies, while a hands-on phishing simulation can demonstrably improve employees’ ability to identify and report suspicious emails. The key is to tailor your approach to your audience and the specific threats you’re trying to address. A highly technical team will respond differently to training than a less technical administrative team.
Consider the learning styles of your workforce and adapt your training accordingly.
Best Practices for Delivering Effective Security Training
Effective security awareness training isn’t a one-size-fits-all solution. It requires a multi-faceted approach. Regular, short, and engaging training sessions are far more effective than infrequent, lengthy ones. Incorporating real-world examples and case studies, relevant to the organization and employee roles, significantly boosts engagement and knowledge retention. Remember, people are more likely to remember something if it resonates with their daily work experience.
Also crucial is the use of diverse training formats. Mixing up methods—presentations, videos, interactive modules, and quizzes—keeps trainees engaged and caters to various learning styles. Finally, consistent reinforcement is key. Don’t just deliver training once and forget about it. Regular refreshers and updates are essential to maintain awareness and adapt to evolving threats.
Sample Security Awareness Training Agenda
A typical training agenda might look something like this:
Module 1: Introduction to Insider Threats (30 minutes)
-Defining insider threats, types of insider threats (malicious, negligent, compromised), and the impact of insider incidents. This module would include a short video and interactive quiz.
Module 2: Social Engineering Tactics (45 minutes)
-Identifying and avoiding common social engineering techniques (phishing, baiting, pretexting, etc.). This would involve a realistic phishing simulation exercise where employees practice identifying and reporting suspicious emails.
Module 3: Data Loss Prevention (DLP) Measures (45 minutes)
– Understanding data classification, secure data handling practices, and the organization’s DLP policies. This could include a walkthrough of the company’s data security policies and a Q&A session.
Module 4: Access Control and Privileges (30 minutes)
– Understanding the principle of least privilege, password security best practices, and reporting suspicious activity. This module would focus on practical application and real-life scenarios.
Module 5: Security Awareness Best Practices (15 minutes)
-Review of key takeaways, Q&A, and resources for ongoing learning. This would be a wrap-up session to solidify learning and provide ongoing support resources.
Incident Response Procedures
Effective incident response is crucial for minimizing damage and ensuring business continuity when an insider threat materializes. A well-defined plan, regularly tested and updated, is essential for navigating these complex situations. This section details the key components of a robust insider threat incident response plan, focusing on a scenario involving data exfiltration.
Responding to an Insider Threat Incident
Responding to an insider threat incident requires a systematic approach, typically divided into several phases. In the scenario of a disgruntled employee exfiltrating customer data, the response would unfold as follows:
- Preparation: This phase involves proactive measures to minimize the impact of an incident. Actions include:
- Developing and regularly testing the incident response plan.
- Establishing clear roles and responsibilities for incident response team members.
- Ensuring access to necessary tools and resources, such as forensic software and secure data storage.
- Identification: This stage involves detecting the incident. Actions include:
- Monitoring system logs and security alerts for suspicious activity, such as unusual data access patterns or large data transfers.
- Analyzing security information and event management (SIEM) data for anomalies.
- Receiving and investigating reports from employees or customers.
- Containment: This phase focuses on limiting the damage caused by the incident. Actions include:
- Immediately suspending the employee’s access to all company systems and networks.
- Blocking the employee’s IP address and any known exfiltration channels.
- Implementing temporary access restrictions on affected systems and databases.
- Eradication: This involves removing the threat and restoring systems to a secure state. Actions include:
- Conducting a thorough forensic analysis to identify the extent of the breach and the methods used by the employee.
- Revoking all compromised credentials and passwords.
- Patching any vulnerabilities exploited by the employee.
- Recovery: This phase focuses on restoring systems and data to their operational state. Actions include:
- Restoring data from backups, ensuring data integrity.
- Implementing security controls to prevent future similar incidents.
- Notifying affected customers, as appropriate.
- Lessons Learned: This critical phase involves reviewing the incident to identify areas for improvement. Actions include:
- Conducting a post-incident review to analyze the effectiveness of the response.
- Updating the incident response plan based on lessons learned.
- Providing training to employees on security awareness and incident reporting procedures.
Incident Reporting and Documentation
Comprehensive incident reporting and documentation are essential for effective incident response and legal compliance. Maintaining a chain of custody for digital evidence is paramount, involving the use of tamper-evident seals and secure hashing algorithms to ensure data integrity. This documentation serves as evidence in investigations and legal proceedings. Failure to properly document incidents can result in significant legal and financial consequences.
| Incident ID | Date/Time | Type of Incident | Affected Systems | Involved Personnel | Initial Response Actions | Status |
|---|---|---|---|---|---|---|
| INC-2024-10-27-001 | October 27, 2024, 14:30 | Data Exfiltration | Customer Database Server, Network Share | John Smith (Employee), Jane Doe (Security Analyst), David Lee (IT Manager) | Employee access suspended, forensic analysis initiated, law enforcement notified. | Ongoing Investigation |
Insider Threat Incident Response Plan Flowchart
A flowchart would visually represent the steps Artikeld above, showing the sequential nature of the response and the decision points along the way. For example, the flowchart would start with “Incident Detected?” leading to either “No” (return to monitoring) or “Yes” (proceed to Containment). Each phase would then be represented by a series of actions, with clear transitions between phases.
The final box would be “Lessons Learned & Plan Update”.
Sample Incident Report
This section would include a sample incident report based on the scenario described earlier, using the table format shown above. Specific details, including timestamps and names of individuals involved, would be included, but placeholder names would be used if necessary to protect privacy.
Key Performance Indicators (KPIs)
Measuring the effectiveness of the incident response plan requires establishing Key Performance Indicators (KPIs). Five examples include:
- Mean Time To Detection (MTTD): The average time taken to detect an incident. Measured by tracking the time between the occurrence of the incident and its detection. A lower MTTD indicates a more effective monitoring system.
- Mean Time To Response (MTTR): The average time taken to respond to an incident. Measured by tracking the time between detection and the initiation of containment actions. A lower MTTR indicates a more efficient response.
- Mean Time To Recovery (MTTR): The average time taken to recover from an incident. Measured by tracking the time from the initiation of recovery actions to full system restoration. A shorter MTTR indicates faster recovery.
- Incident Resolution Rate: The percentage of incidents successfully resolved. Measured by dividing the number of resolved incidents by the total number of incidents. A higher rate indicates effective resolution.
- Cost of Incidents: The total cost associated with each incident, including investigation, remediation, and potential legal fees. Measured by tracking all expenses related to each incident. A lower cost per incident indicates effective cost management.
Addressing Legal and Regulatory Obligations
The incident response plan must address the organization’s legal and regulatory obligations. In the scenario of a data breach involving sensitive personal information, regulations such as GDPR (General Data Protection Regulation), CCPA (California Consumer Privacy Act), and HIPAA (Health Insurance Portability and Accountability Act) – depending on the nature of the data and the organization’s location and industry – would be relevant.
The plan should Artikel procedures for notifying affected individuals and authorities, as required by these regulations.
“Our insider threat response prioritizes swift, decisive action to mitigate risk, protect sensitive data, and maintain operational resilience. We are committed to full transparency and compliance with all relevant regulations.”
Risk Assessment and Mitigation
This section delves into the crucial aspects of identifying, assessing, and mitigating insider threats within two distinct organizational contexts: a medium-sized regional hospital and a fintech startup. We’ll explore various risk assessment methodologies, compare mitigation strategies, and develop a prioritized implementation plan, including monitoring and evaluation.
Potential Insider Threats in a Regional Hospital and Fintech Startup
Let’s consider a medium-sized regional hospital with 500 employees and a fintech startup with 50 employees. In the hospital, departments like pharmacy, medical records, and billing are particularly vulnerable. In the fintech startup, software development, finance, and security teams face higher risks.
- Hospital:
- Scenario 1: A disgruntled pharmacy technician diverts controlled substances for personal use or sale, leading to patient harm and legal repercussions.
- Scenario 2: A billing clerk alters patient records to inflate charges, resulting in financial fraud and potential legal action.
- Scenario 3: A medical records employee sells patient data to a third party, leading to significant privacy breaches and reputational damage.
- Scenario 4: A disgruntled nurse alters patient medical records to sabotage a colleague, leading to potential misdiagnosis and treatment delays.
- Scenario 5: An IT employee with access to the hospital network installs malware, causing system disruption and data loss.
- Fintech Startup:
- Scenario 1: A disgruntled software developer inserts malicious code into the company’s application, leading to financial losses and reputational damage.
- Scenario 2: A finance employee embezzles funds through fraudulent transactions, causing significant financial losses.
- Scenario 3: A security employee compromises the company’s security systems, allowing unauthorized access to sensitive data.
- Scenario 4: A disgruntled employee leaks confidential information about the company’s financial performance or upcoming product launches, impacting investor confidence and market share.
- Scenario 5: An employee with access to customer data sells this information to a competitor, resulting in loss of customers and potential legal action.
Risk Assessment Methodologies
Several methodologies can be employed for insider threat risk assessment. Each has strengths, weaknesses, and specific data requirements.
- Qualitative Risk Assessment: This approach relies on expert judgment and experience to assess the likelihood and impact of insider threats. Strengths include simplicity and ease of use, while weaknesses include subjectivity and lack of quantitative data. In the hospital, experts might rank the likelihood of a pharmacy technician diverting drugs as high, based on past incidents and knowledge of the pressures faced by such staff.
Data required would be expert opinions, historical incident data, and employee surveys.
- Quantitative Risk Assessment: This methodology uses numerical data to assign probabilities and impacts to insider threats. Strengths include objectivity and the ability to quantify risk, but weaknesses include the need for extensive data and complexity. For the fintech startup, this approach might involve calculating the financial loss associated with a data breach based on the number of compromised records and the cost of remediation.
Data needed includes historical incident data, financial data, and estimates of recovery costs.
- Hybrid Risk Assessment: This combines qualitative and quantitative methods to leverage the strengths of both. Strengths include a more balanced and comprehensive view of risk, but weaknesses include the complexity of integrating different data types. For both organizations, this approach might use expert judgment to assess the likelihood of certain events and then use quantitative data to assess the potential financial impact.
Data needed is a combination of expert opinions, historical data, and financial data.
Risk Mitigation Strategies Comparison
| Strategy Name | Description | Cost | Effectiveness | Best Suited Scenario |
|---|---|---|---|---|
| Access Control | Restricting access to sensitive data and systems based on roles and responsibilities. | Medium | High | Hospital Scenarios 2, 3, 5; Fintech Scenarios 1, 2, 4 |
| Data Loss Prevention (DLP) | Implementing tools and techniques to prevent sensitive data from leaving the organization’s control. | High | High | Hospital Scenarios 3; Fintech Scenarios 1, 4 |
| Employee Monitoring | Monitoring employee activity on company systems and networks. | Medium | Medium | Hospital Scenarios 1, 2, 4; Fintech Scenarios 1, 2 |
| Security Awareness Training | Educating employees about insider threats and security best practices. | Low | Medium | All Scenarios |
| Background Checks | Conducting thorough background checks on prospective employees. | Medium | Medium | All Scenarios |
Prioritized Risk Mitigation Strategies
For both the hospital and the fintech startup, the top three prioritized strategies are: Access Control (High effectiveness, Medium cost), Data Loss Prevention (High effectiveness, High cost), and Security Awareness Training (Medium effectiveness, Low cost). This prioritization balances effectiveness with cost-efficiency, addressing both immediate and long-term risks.
Understanding insider threat awareness is crucial for organizational security, and comprehensive exam preparation is essential. Resources such as the genesys cloud knowledge base , while not directly focused on security awareness training, might offer insights into related areas like data management and access control, which are indirectly relevant to insider threat prevention. Therefore, a multi-faceted approach to studying for insider threat awareness exams is recommended, incorporating diverse sources of information.
Implementation Plan for Top Three Strategies
- Access Control:
- Step 1: Conduct a comprehensive access review (Timeline: 2 months, Responsible Party: IT Department, Resources: Access management tools).
- Step 2: Implement role-based access control (RBAC) (Timeline: 3 months, Responsible Party: IT Department, Resources: RBAC software).
- Step 3: Regularly audit access privileges (Timeline: Ongoing, Responsible Party: IT Department, Resources: Audit logs).
- Data Loss Prevention:
- Step 1: Identify sensitive data (Timeline: 1 month, Responsible Party: Data Security Officer, Resources: Data discovery tools).
- Step 2: Implement DLP tools (Timeline: 2 months, Responsible Party: IT Department, Resources: DLP software).
- Step 3: Regularly review and update DLP policies (Timeline: Ongoing, Responsible Party: Data Security Officer, Resources: DLP management console).
- Security Awareness Training:
- Step 1: Develop engaging training materials (Timeline: 1 month, Responsible Party: HR Department, Resources: Training platform).
- Step 2: Conduct mandatory training sessions (Timeline: 1 month, Responsible Party: HR Department, Resources: Training room, instructors).
- Step 3: Conduct regular refresher training (Timeline: Ongoing, Responsible Party: HR Department, Resources: Online training modules).
Challenges in Implementing Risk Mitigation Strategies and Proposed Solutions
- Budget Constraints: Implementing robust security measures can be expensive. Solution: Prioritize strategies based on cost-effectiveness, seeking grants or external funding.
- Employee Resistance: Employees may resist new security measures, perceiving them as intrusive or inconvenient. Solution: Clearly communicate the rationale behind the measures, emphasizing the benefits of enhanced security and data protection.
- Lack of Expertise: Implementing and managing security measures requires specialized skills and knowledge. Solution: Hire security professionals or contract with external security firms to provide expertise and support.
Monitoring and Evaluation Plan: This plan will track the effectiveness of the implemented mitigation strategies. Key Performance Indicators (KPIs) will include the number of security incidents, the number of data breaches, the number of employees completing security awareness training, and the average time to detect and respond to security incidents. Reports will be generated monthly by the IT and Security Departments, with quarterly reviews by senior management. Continuous monitoring of access logs and DLP alerts will provide real-time insights into potential threats. The plan will be reviewed and updated annually based on performance data and evolving threats.
Physical Security Measures
Physical security is often overlooked in insider threat discussions, but it’s a crucial first line of defense. Strong physical security measures significantly reduce opportunities for malicious insiders to access sensitive data or equipment, thereby minimizing the risk of data breaches, sabotage, or espionage. This section details the importance of physical security, methods for securing sensitive areas and equipment, and examples of effective deterrent measures.
Importance of Physical Security in Preventing Insider Threats
Insider threats related to physical access represent a significant vulnerability. Unauthorized access to data centers, server rooms, or even filing cabinets containing sensitive documents can lead to devastating consequences. For example, a disgruntled employee with physical access could steal intellectual property, compromising years of research and development, resulting in significant financial losses and reputational damage. A case study of a company experiencing a data breach due to an insider gaining unauthorized physical access to a server room illustrates the potential for substantial financial penalties, legal ramifications, and loss of customer trust.
Effective physical security directly correlates with a reduction in insider threat incidents. While external threats require perimeter security, insiders already possess legitimate access, making strong internal physical security paramount. The challenges differ; external threats try to breach perimeters, while insiders exploit existing access. Thus, physical security’s effectiveness against insiders focuses on controlling internal movement and access to sensitive resources.
Securing Sensitive Areas and Equipment
Securing sensitive areas requires a multi-layered approach. Access control systems, such as key card access, biometric authentication (fingerprint or retinal scans), and multi-factor authentication (requiring multiple forms of verification), restrict entry. Surveillance systems, including strategically placed CCTV cameras with recording and monitoring capabilities, provide a visual deterrent and record suspicious activity. Alarm systems, triggered by unauthorized entry or tampering, alert security personnel.The table below compares the cost-effectiveness and security levels of different access control systems.| Access Control System | Cost (Relative) | Security Level (High/Medium/Low) | Advantages | Disadvantages ||—|—|—|—|—|| Key Card Access | Low | Medium | Simple, widely available, relatively inexpensive | Easily duplicated, susceptible to theft or loss, requires careful management of keys || Biometric Authentication | High | High | Highly secure, difficult to replicate, strong user authentication | Can be expensive to implement and maintain, privacy concerns regarding data storage, potential for false positives/negatives || Multi-Factor Authentication | Medium | High | Strong security, reduces risk significantly, adds an extra layer of verification | Can be inconvenient for users, requires additional infrastructure and software |Securing sensitive equipment involves physical locking mechanisms (cable locks, keyed cabinets), tamper-evident seals (that visibly indicate if a device has been opened), and environmental controls (climate-controlled rooms for servers to prevent overheating and data loss).The following flowchart illustrates the process of securing a server room:[Description of Flowchart: The flowchart would begin with “Server Room Access Request,” branching to “Authorize Access (through Access Control System)” and “Deny Access (log reason).” Authorized access leads to “Entry via Keycard/Biometric Scan,” followed by “CCTV Monitoring Initiated” and “Environmental Monitoring Initiated.” A separate branch from “Deny Access” leads to “Security Alert.” All paths converge at “Server Room Secured.”]
Examples of Physical Security Measures that Deter Insider Threats
Several physical security measures deter insider threats. Preventative measures aim to stop incidents before they occur, while detective measures help identify and respond to incidents after they happen.| Physical Security Measure | Target Threat Vector | Effectiveness (High/Medium/Low) | Implementation Details ||—|—|—|—|| CCTV Surveillance | Data theft, sabotage, espionage | High | Strategic placement of cameras covering all entry/exit points and sensitive areas, 24/7 monitoring with recording capabilities, integration with alarm systems for immediate response || Access Control System (Multi-Factor Authentication) | Unauthorized access, data theft | High | Key card access combined with biometric authentication or one-time passwords, robust access control lists, regular audits of access privileges || Tamper-Evident Seals | Data theft, sabotage | Medium | Seals on sensitive equipment, cabinets, and data storage devices; alarms triggered upon tampering, regular inspection of seals || Environmental Controls (HVAC systems with monitoring) | Data loss, equipment damage | Medium | Temperature and humidity monitoring and control within specified ranges for optimal equipment operation and data integrity, regular maintenance and calibration || Security Guards (physical patrols and monitoring) | All threat vectors | High | Patrolling sensitive areas, monitoring access points, responding to alarms, visitor management, regular shift changes to prevent collusion |Regular audits and inspections are crucial.
These involve physical checks of security measures, review of access logs, testing of alarm systems, and verification of environmental controls. Reports detail findings, identify vulnerabilities, and recommend improvements.
Policy and Procedure Enforcement
Effective security policies are the bedrock of a strong insider threat program. Without clear, well-defined, and consistently enforced policies, even the best technology and training can be rendered ineffective. This section will explore the critical role of policy and procedure enforcement in mitigating insider threats.
The Importance of Clear and Enforceable Security Policies
Clear and enforceable security policies are vital for several reasons. First, they significantly reduce risk by establishing acceptable use guidelines, access controls, and data handling procedures. This proactive approach helps prevent many insider threat incidents before they occur. Second, strong policies demonstrate legal compliance, helping organizations avoid hefty fines and reputational damage. Regulations like GDPR (General Data Protection Regulation), CCPA (California Consumer Privacy Act), and HIPAA (Health Insurance Portability and Accountability Act) all mandate specific data security practices, and robust policies are crucial for demonstrating adherence.
For example, a data breach resulting from a failure to comply with GDPR could lead to fines of up to €20 million or 4% of annual global turnover – a significant financial penalty. Finally, clear policies streamline operations by providing employees with a clear understanding of their responsibilities, reducing ambiguity and improving overall efficiency. This clarity minimizes confusion and the potential for accidental data breaches due to misunderstandings.
Conversely, unclear or unenforceable policies create a breeding ground for confusion, inconsistent practices, and ultimately, increased risk. They offer little guidance, fail to deter malicious actors, and provide weak legal defense in the event of a breach.
Methods for Ensuring Policy Compliance
A multi-faceted approach is needed to ensure compliance with security policies. The following table Artikels various methods and their associated strengths and weaknesses:
| Method | Description | Advantages | Disadvantages | Implementation Considerations |
|---|---|---|---|---|
| Regular Audits | Scheduled reviews of security practices and policy adherence. | Identifies gaps and non-compliance. Provides a documented record of compliance efforts. | Can be resource-intensive. May disrupt operations if not planned carefully. | Define audit frequency, scope, and reporting. Use a standardized checklist. Ensure auditor independence. |
| Training and Awareness | Educating employees on security policies and best practices. | Improves understanding and compliance. Fosters a security-conscious culture. | Requires ongoing effort and reinforcement. Effectiveness can be difficult to measure directly. | Track completion rates and measure effectiveness through quizzes and simulated phishing attacks. Use various training methods (e.g., videos, interactive modules, in-person sessions). |
| Monitoring and Logging | Tracking user activity and system events to detect policy violations. | Provides real-time alerts and evidence. Enables proactive threat detection. | Can generate large amounts of data. Requires skilled personnel to analyze logs effectively. | Implement effective logging and alert systems. Develop clear escalation procedures for alerts. Regularly review and analyze logs. |
| Access Control Lists (ACLs) | Restricting access to sensitive resources based on roles and permissions. | Prevents unauthorized access. Limits the potential impact of a compromised account. | Can be complex to manage. Requires careful planning and regular review. | Regularly review and update ACLs. Implement the principle of least privilege. Use role-based access control (RBAC). |
| Automated Enforcement | Using tools to automatically enforce policies (e.g., DLP). | Reduces manual effort and improves consistency. Provides immediate feedback on policy violations. | Requires investment in technology. May require integration with existing systems. | Choose tools that integrate with existing systems. Configure alerts and responses appropriately. Regularly review and update tool configurations. |
Sample Security Policy Addressing Insider Threats
This sample policy Artikels measures to address insider threats within a medium-sized organization.
1. Definition of Insider Threat
An insider threat is any employee, contractor, or other individual with authorized access who intentionally or unintentionally compromises organizational security, resulting in data breaches, system disruptions, or other harmful actions. This includes malicious intent, negligence, and accidental errors.
2. Risk Assessment
Regular risk assessments will identify potential insider threat vectors, such as access to sensitive data, privileged accounts, and vulnerabilities in systems and processes. These assessments will consider employee roles, responsibilities, and access privileges.
3. Prevention Measures
Thorough background checks for all employees and contractors.
Strict access control policies based on the principle of least privilege.
Implementation of Data Loss Prevention (DLP) tools to monitor and prevent sensitive data exfiltration.
Comprehensive security awareness training programs covering social engineering, phishing, and safe data handling practices.
Regular security audits and vulnerability assessments.
Implementation of multi-factor authentication (MFA) for all accounts.
Separation of duties to prevent single points of failure and fraud.
Job rotation for sensitive roles to reduce the risk of collusion and fraud.
4. Detection Measures
Continuous monitoring of user activity, including login attempts, file access, and data transfers.
Regular analysis of system logs to identify suspicious patterns and anomalies.
Implementation of anomaly detection systems to flag unusual behavior.
Regular security audits to assess compliance with security policies.
5. Incident Response Plan
Establish clear reporting procedures for suspected insider threats.
Develop a detailed investigation process, including forensic analysis and interviewing techniques.
Define remediation actions, such as account suspension, system restoration, and data recovery.
Implement communication protocols to inform relevant stakeholders.
6. Disciplinary Actions
Violations of this policy will result in disciplinary actions, ranging from warnings and mandatory retraining to suspension and termination of employment, depending on the severity of the violation.
Monitoring and Detection Techniques
Keeping tabs on what your employees are doing might sound a little Big Brother-ish, but in the world of cybersecurity, it’s a crucial part of protecting your organization from insider threats. Effective monitoring allows us to identify suspicious activities before they escalate into major data breaches or other damaging events. It’s about striking a balance between security and employee privacy, of course.We’ll explore various methods for monitoring user activity, focusing on how they help pinpoint potential threats.
We’ll also look at indicators of compromise (IOCs) – the telltale signs that something’s gone wrong – and delve into the world of Security Information and Event Management (SIEM) systems.
User Activity Monitoring Methods
Several methods exist to monitor user activity without invading employee privacy excessively. These methods provide different levels of detail and require careful consideration of ethical and legal implications. For example, implementing robust logging and auditing capabilities across all systems is a fundamental starting point. This includes detailed logs of login attempts, file access, data transfers, and system modifications.
Real-time monitoring tools can provide immediate alerts on suspicious activity, allowing for quicker responses. User and Entity Behavior Analytics (UEBA) goes a step further, using machine learning to establish baselines of normal user behavior and then flag deviations from that norm as potential threats. Finally, network traffic analysis can highlight unusual communication patterns or data exfiltration attempts.
Key Indicators of Compromise (IOCs) Related to Insider Threats
Recognizing the signs of a potential insider threat is critical. IOCs can be subtle or blatant, depending on the sophistication of the threat actor. Some common indicators include unusual access patterns, such as accessing sensitive data outside of normal working hours or from unusual locations. A sudden spike in data transfers, especially large volumes of data being copied or moved to external locations, is another red flag.
Attempts to disable security systems or bypass access controls should also raise serious concerns. Finally, changes to system configurations or the creation of unauthorized accounts can indicate malicious intent. Detecting these IOCs requires a multi-faceted approach, combining automated monitoring tools with human oversight.
Security Information and Event Management (SIEM) Systems Comparison
SIEM systems are the central nervous system of many organizations’ security posture. They collect and analyze security logs from various sources, correlating events to identify potential threats. Different SIEM systems vary in their capabilities, scalability, and cost. Some are cloud-based, offering flexibility and scalability, while others are on-premise, providing more control but potentially higher maintenance costs. Some systems excel at real-time threat detection, while others are better suited for post-incident analysis.
The choice of SIEM system depends on the specific needs and resources of the organization. Factors to consider include the volume of logs generated, the need for real-time threat detection, and the level of expertise available for system management and analysis. A proper comparison should also take into account the integration capabilities with other security tools, the user interface’s ease of use, and the vendor’s reputation and support services.
Legal and Ethical Considerations: Insider Threat Awareness Exam Answers

Navigating the complex world of insider threats requires a keen understanding of both the legal and ethical ramifications. Organizations face significant legal liabilities following data breaches, while simultaneously needing to uphold the ethical rights of their employees. Striking a balance between these competing interests is crucial for responsible security management.
Legal Ramifications of Insider Threats and Data Breaches
Understanding the legal landscape surrounding insider threats is paramount. Organizations must be prepared to navigate data breach notification laws, potential civil lawsuits, and the possibility of criminal prosecution. Failure to comply with these legal obligations can result in severe financial penalties and reputational damage.
Data Breach Notification Laws
Data breach notification laws vary significantly by jurisdiction, mandating timely notification of affected individuals and regulatory bodies. For example, the General Data Protection Regulation (GDPR) in the European Union requires notification within 72 hours of becoming aware of a breach. In contrast, the California Consumer Privacy Act (CCPA) has its own specific requirements. HIPAA, governing healthcare data, imposes stringent notification rules with significant penalties for non-compliance.
The information included in these notifications typically includes the nature of the breach, the types of data affected, and steps individuals can take to mitigate potential harm. Failure to meet these deadlines can lead to substantial fines.
Civil Liability
Organizations and individuals can face civil lawsuits following insider threats resulting in data breaches. These lawsuits often allege negligence, breach of contract, or other torts, seeking compensation for financial losses, reputational harm, and emotional distress suffered by victims. The success of such lawsuits depends on proving the organization’s failure to implement reasonable security measures to prevent the breach and demonstrating a direct causal link between the breach and the claimed damages.
For instance, a company might be sued for failing to adequately train employees on security protocols, leading to a data breach that caused significant financial losses for a client.
Criminal Prosecution
Insiders involved in data breaches can face criminal charges under various statutes, such as the Computer Fraud and Abuse Act (CFAA) in the United States. These charges can range from misdemeanors to felonies, depending on the severity of the offense and the resulting damages. Examples include unauthorized access to computer systems, theft of trade secrets, and intentional destruction of data.
Penalties can include substantial fines, imprisonment, and a criminal record, significantly impacting the individual’s future prospects.
Ethical Considerations When Dealing with Suspected Insider Threats
Addressing suspected insider threats ethically requires a delicate balance between protecting organizational assets and upholding the rights of employees. This involves ensuring due process, navigating the privacy versus security dilemma, and providing robust whistleblower protection.
Due Process
Employees suspected of insider threats are entitled to due process, including the right to be informed of accusations, the opportunity to respond to those accusations, and fair treatment throughout the investigation. This ensures that accusations are handled fairly and prevents wrongful accusations from damaging an employee’s reputation or career. A thorough investigation, conducted in a fair and impartial manner, is essential to uphold due process.
Privacy vs. Security
Balancing employee privacy with the need to protect organizational data presents a significant ethical challenge. Organizations must carefully consider what data is necessary to collect during an investigation and avoid collecting unnecessary personal information. For example, monitoring an employee’s internet activity might be justified if there is reasonable suspicion of data exfiltration, but monitoring their personal emails would likely be an overreach.
This balance requires a careful assessment of the potential risks and benefits of each investigative action.
Whistleblower Protection
Organizations should establish clear and accessible reporting mechanisms for employees to report suspected insider threats without fear of retaliation. Protecting whistleblowers is crucial for maintaining a culture of security awareness and preventing future incidents. Strong whistleblower protection policies, combined with thorough investigations of reported incidents, demonstrate a commitment to ethical conduct and contribute to a safer work environment.
Retaliation against whistleblowers can lead to legal challenges and damage the organization’s reputation.
Maintaining Employee Privacy While Conducting Investigations
Investigations into suspected insider threats must be conducted while respecting employee privacy rights. This involves employing principles of data minimization, transparency, and secure data handling.
Data Minimization
During investigations, only data necessary to address the suspected threat should be collected. This principle minimizes the risk of inadvertently collecting sensitive personal information that is not relevant to the investigation. For example, if the investigation focuses on data exfiltration, accessing an employee’s personal social media accounts would likely be considered unnecessary and a violation of privacy.
Transparency and Consent
Employees should be informed about the investigation and the reasons for data collection whenever possible. Obtaining informed consent before accessing personal data is crucial, especially for sensitive information. Transparency builds trust and reduces the likelihood of legal challenges. For instance, informing an employee that their work computer will be examined as part of an investigation is a necessary step in maintaining transparency.
Data Security and Retention
Data collected during investigations must be securely stored and managed, utilizing encryption, access controls, and data retention policies. A clear policy outlining how long data will be retained and how it will be securely disposed of afterward is crucial for protecting employee privacy and complying with relevant regulations. The table below summarizes best practices.
| Best Practice | Description | Implementation Example |
|---|---|---|
| Data Encryption | Encrypt all sensitive data collected during the investigation. | Use AES-256 encryption for all data at rest and in transit. |
| Access Control | Limit access to investigation data to authorized personnel only. | Implement role-based access control (RBAC) to restrict access based on job responsibilities. |
| Data Retention Policy | Establish a clear policy for how long investigation data will be retained and securely disposed of afterward. | Retain data for a maximum of three years, then securely delete it. |
| Regular Security Audits | Conduct regular audits to ensure the security of investigation data. | Conduct audits at least annually, with reports reviewed by legal counsel. |
Future Trends in Insider Threat Management

The landscape of insider threats is constantly evolving, driven by technological advancements, shifting work patterns, and increasingly sophisticated attack methods. Effectively managing these threats requires a proactive and adaptable approach, leveraging emerging technologies and strategies while acknowledging the unique challenges of the modern workplace. This section will explore some key future trends in insider threat management.
Emerging Technologies and Strategies for Managing Insider Threats
The fight against insider threats is becoming increasingly reliant on advanced technologies. Behavioral analytics, for example, are moving beyond simple rule-based systems to incorporate machine learning algorithms that can identify subtle anomalies in user activity indicative of malicious intent. This allows for earlier detection of threats before significant damage occurs. Furthermore, advancements in data loss prevention (DLP) are focusing on context-aware solutions, which go beyond simply blocking specific file types to understand the sensitivity of data and the context of its transmission.
This allows for a more nuanced approach, minimizing false positives and maximizing detection accuracy. Another significant development is the integration of threat intelligence feeds into security information and event management (SIEM) systems, providing a broader context for analyzing user behavior and identifying potential insider threats. These feeds can alert organizations to emerging threats and vulnerabilities, allowing for proactive mitigation strategies.
Challenges of Managing Insider Threats in a Remote Work Environment
The widespread adoption of remote work has significantly broadened the attack surface for insider threats. Monitoring employee activity and enforcing security policies becomes significantly more complex when employees are working from various locations and using diverse devices. The lack of physical controls makes it harder to prevent unauthorized access to sensitive data and equipment. Additionally, remote workers may be less likely to report suspicious activity due to a perceived lack of immediate supervision or fear of retribution.
This highlights the critical need for robust remote access security measures, strong cybersecurity awareness training, and effective communication channels for reporting security incidents. Organizations need to implement comprehensive remote access policies that include multi-factor authentication, secure remote desktop protocols, and regular security audits of remote work setups. Strong emphasis on employee training and open communication is also vital to building a security-conscious culture in a distributed workforce.
Consider, for example, a company that implemented a remote access policy that included mandatory multi-factor authentication and regular security awareness training. This significantly reduced their vulnerability to insider threats related to compromised credentials and phishing attacks.
Artificial Intelligence in Insider Threat Detection
Artificial intelligence (AI) is rapidly transforming insider threat detection capabilities. AI-powered systems can analyze vast amounts of data from various sources – including user activity logs, network traffic, and email communications – to identify patterns and anomalies that might indicate malicious intent. Unlike traditional rule-based systems, AI can adapt to evolving threat patterns and learn from new data, improving its accuracy over time.
For instance, AI can identify unusual access patterns, such as accessing sensitive data outside of normal working hours or downloading large volumes of data shortly before termination. AI can also help prioritize alerts, focusing on the most critical threats and reducing the burden on security analysts. This enables security teams to respond more efficiently and effectively to potential insider threats.
Imagine an AI system detecting a pattern of unusual file access by an employee who is about to be laid off. The system could flag this activity as high-risk, allowing security personnel to investigate promptly and potentially prevent data exfiltration.
Q&A
What are the most common types of insider threat incidents?
Common incidents include data theft, sabotage, espionage, and accidental data breaches resulting from negligence or lack of awareness.
How can I improve the effectiveness of security awareness training?
Use interactive modules, simulations, and regular refresher training. Tailor content to specific roles and responsibilities, and measure training effectiveness through assessments and post-training behavior changes.
What are some key indicators of compromise (IOCs) related to insider threats?
IOCs include unusual access patterns, data exfiltration attempts, unauthorized software installations, and changes to system configurations.
What is the role of forensic investigation in insider threat incidents?
Forensic investigations determine the extent of damage, identify the perpetrator, gather evidence for legal action, and inform future preventative measures.
How can I balance employee privacy with the need to protect organizational data?
Implement data minimization principles, obtain informed consent when appropriate, and adhere strictly to relevant privacy regulations like GDPR and CCPA.


